Introduction
Wireshark 4.2.0 added a new functionality [1] that can be used to directly launch a
web browser with the SSLKEYLOGFILE environment variable set, in order to
easily sniff and decrypt TLS traffic from a started application.
Howto
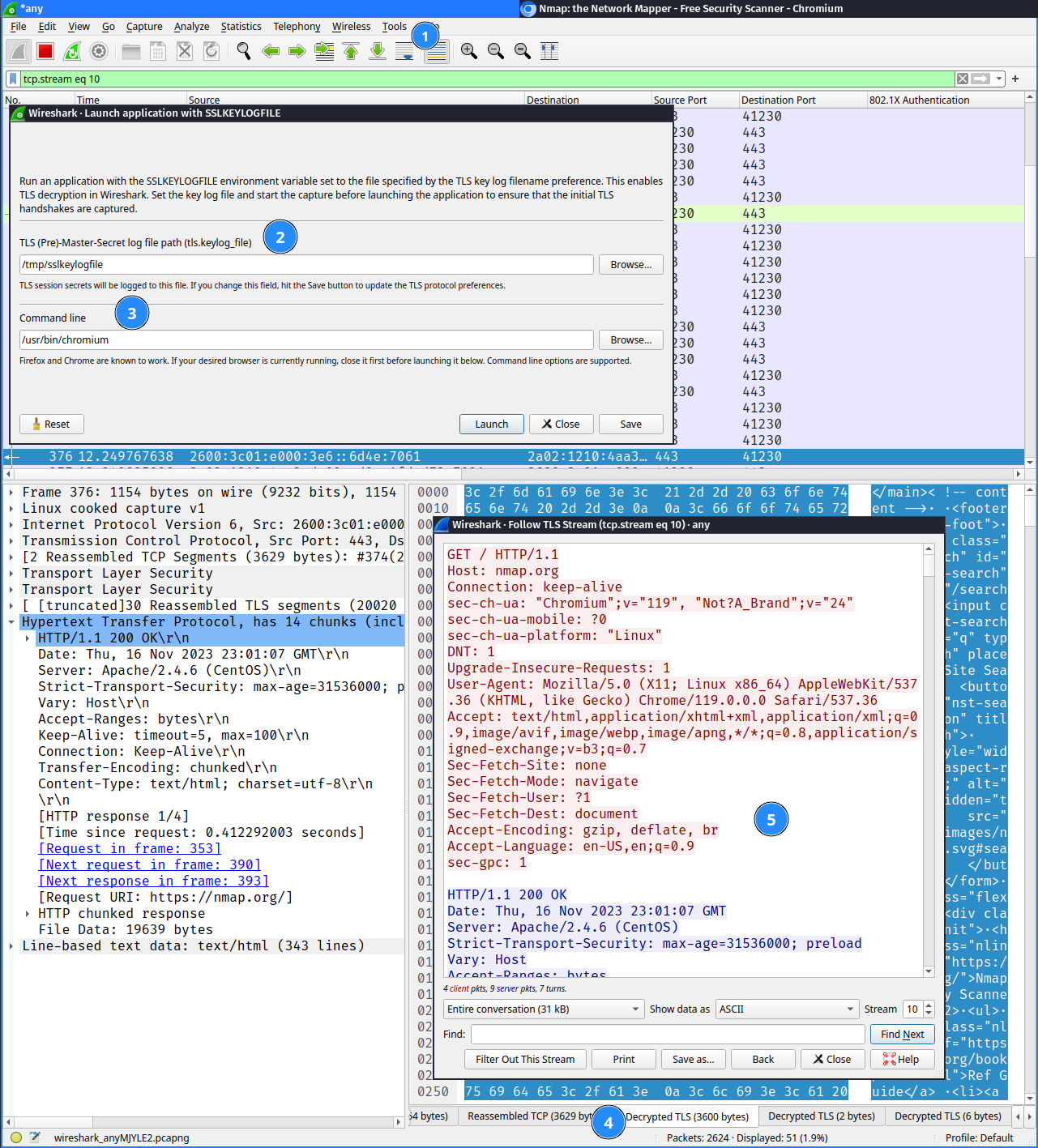
This new feature can be found in the Tools menu and then under TLS Keylog Launcher (1).
You can specify to which file where the SSLKEYLOGFILE variable
should point to (2) in order to save the key material. Then, a command can be
provided in the command line input field (3), which is then started with the
SSLKEYLOGFILE variable set. If an application supports the SSLKEYLOGFILE
mechanism [3], the TLS keys are the automatically stored in the configured file and
Wireshark is able to decrypt the content (4) and show it in cleartext (5).
References
- [1] Wireshark 4.2.0 Release Notes: https://www.wireshark.org/docs/relnotes/wireshark-4.2.0.html
- [2] Wireshark Documentation of the Menu Item: https://www.wireshark.org/docs/wsug_html_chunked/ChUseToolsMenuSection.html
- [3] IETF Draft “The SSLKEYLOGFILE Format for TLS”: https://www.ietf.org/archive/id/draft-thomson-tls-keylogfile-00.html